As blockchain technology and decentralised finance (DeFi) continue to evolve, the importance of securing digital assets becomes paramount. Web3 wallets, which serve as the gateways to decentralised environments, require robust security measures to protect users' funds from potential threats. This article explores the crucial aspects of Web3 wallet security and provides actionable insights for protecting digital assets in decentralised environments.
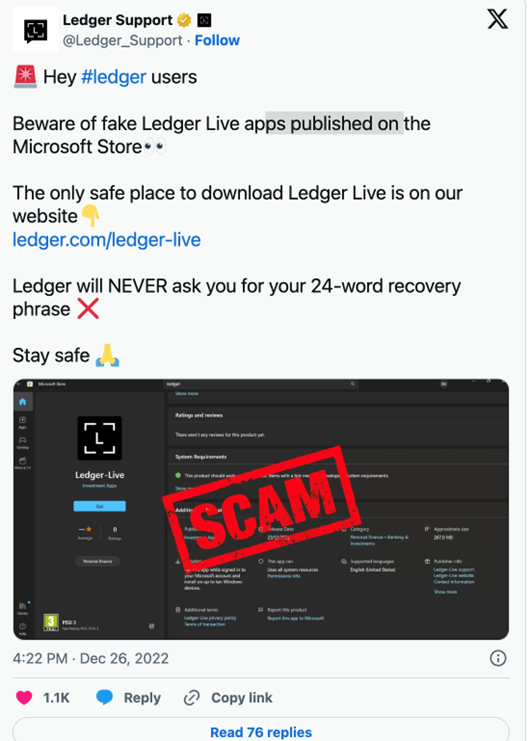
Figure 2: The official Ledger support social media account warned users about a fake ledger application that was published on Microsoft App Store.
Source: https://cointelegraph.com/news/fake-ledger-live-app-sneaks-into-microsoft-app-store-as-victims-lose-half-a-million
In November 2023, a similar incident occurred involving a fake Ledger application on the Microsoft App Store. The total amount of stolen assets was roughly 16.8 BTC, worth around $588K at that time. This event underscored several key lessons:
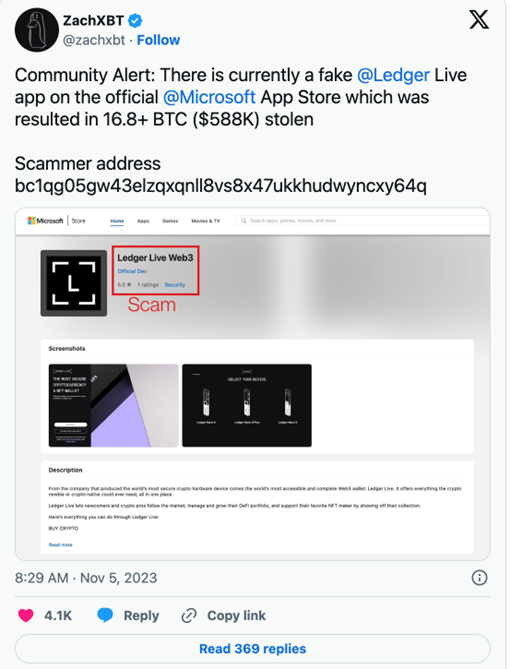
Figure 3: A similar incident involving a fake Ledger application on the Microsoft App Store occurred in November 2023.
Source: https://cointelegraph.com/news/fake-ledger-live-app-sneaks-into-microsoft-app-store-as-victims-lose-half-a-million
What is a Web3 Wallet?
Web3 wallets are digital tools that allow users to interact with decentralised applications (dApps) and manage their cryptocurrencies. Unlike traditional wallets, Web3 wallets operate on blockchain technology, providing users with complete control over their assets without relying on intermediaries like banks. This decentralisation enhances privacy and security but also places the responsibility of securing assets squarely on the users.Types of Web3 Wallets
There are several types of web3 wallets in existence, and among these are:- Hot Wallets: These are online wallets accessible via web browsers or mobile apps. Examples include MetaMask and Trust Wallet. While convenient for frequent transactions, they are more vulnerable to hacking attempts due to their constant internet connectivity.
- Cold Wallets: These are offline wallets, such as hardware wallets like Ledger and Trezor. They store private keys offline, significantly reducing the risk of online attacks. However, they require careful handling to avoid physical theft or damage.
- Custodial Wallets: Custodial wallets are managed by third-party services that hold the private keys on behalf of the user. While they offer ease of use, they also come with the risk of the custodian being compromised.
- Non-Custodial Wallets: Non-custodial wallets give users full control over their private keys, providing greater security and privacy but requiring users to take full responsibility for safeguarding their keys.
- Multi-Signature Wallets (Multi-sig): Multi-signature wallets require multiple private keys to authorise a transaction. This adds an extra layer of security, especially for organisational use or large funds. Examples include Gnosis Safe and BitGo.
Key Security Threats to Web3 Wallets
Some of the critical security concerns regarding web3 wallets include the following:- Phishing Attacks: Attackers create fake websites or emails that mimic legitimate services to trick users into revealing their private keys or seed phrases.
- Social Engineering: Attackers manipulate users into divulging their private information through psychological tricks.
- Man-in-the-Middle (MITM) Attacks: Hackers intercept communication between a user and a Web3 service to steal credentials or manipulate transactions.
- Malware: Malicious software can be used to steal private keys from hot wallets or intercept transactions.
- Smart Contract Vulnerabilities: Bugs in smart contracts can be exploited to drain funds from wallets interacting with these contracts.
Best Practices for Securing Web3 Wallets
- Use Hardware Wallets: For substantial amounts of digital assets, hardware wallets offer the highest level of security by keeping private keys offline. Users are recommended to only purchase hardware wallets from official manufacturers or trusted retailers to avoid tampered devices. From the picture below, the hardware wallet on the left side is genuine while the hardware wallet on the right side has been tampered with.
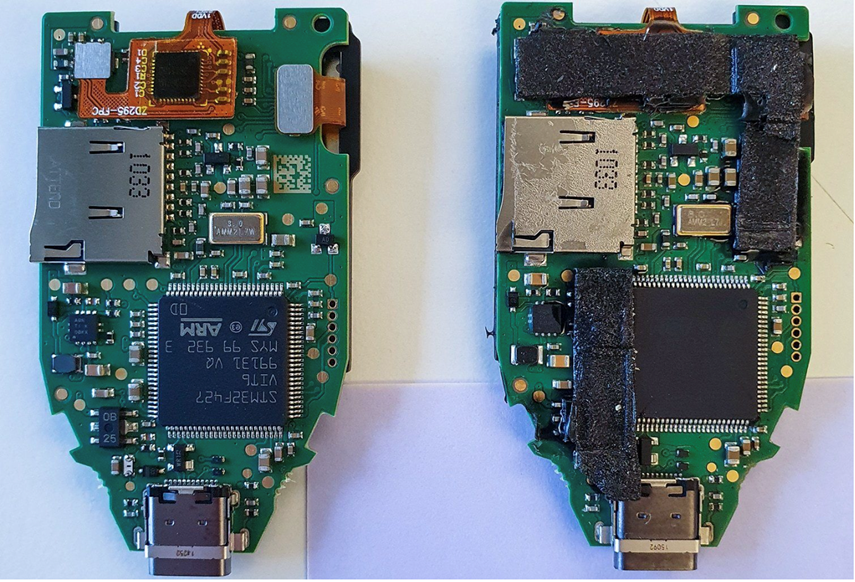 Figure 1: Genuine (left) versus tampered (right) hardware wallets.Source: https://www.kaspersky.com/blog/fake-trezor-hardware-crypto-wallet/48155/
Figure 1: Genuine (left) versus tampered (right) hardware wallets.Source: https://www.kaspersky.com/blog/fake-trezor-hardware-crypto-wallet/48155/ - Enable Two-Factor Authentication (2FA): Adding an extra layer of security to your wallet can protect against unauthorised access, especially for hot wallets.3. Verify URLs and Sources: Always double-check the URL of the website you are accessing to ensure it is legitimate. Avoid clicking on links from unsolicited emails or messages.
- Regularly Update Software: Ensure that your wallet software, browser, and any related applications are up-to-date to protect against known vulnerabilities.
- Backup Your Seed Phrase: Store your seed phrase in a secure, offline location. This is crucial for recovering your wallet if you lose access to it.
- Use Strong Passwords: Ensure your passwords are complex and unique for each service. Consider using a password manager to keep track of them.
- Be Cautious with Public Wi-Fi: Avoid accessing your Web3 wallet over public Wi-Fi networks, which are often insecure and prone to MITM attacks.
- Monitor for Suspicious Activity: Regularly check your wallet and transaction history for any unauthorised or unusual activities.
Case Studies and Lessons Learned
Learning from past incidents can provide valuable insights into improving security. Here are some notable case studies:Case Study: The Mt. Gox Hack
In 2014, the Mt. Gox exchange, which once handled over 70% of all Bitcoin transactions, was hacked, resulting in the loss of 850,000 Bitcoins. This event underscored several key lessons:- Importance of Audits and Transparency: Regular audits and transparent operations could have identified vulnerabilities and discrepancies sooner.
- Centralisation Risks: The centralised nature of Mt. Gox made it a prime target. Decentralised exchanges and non-custodial wallets mitigate this risk.
- Regulatory Oversight: Lack of regulatory oversight and proper security measures contributed to the scale of the loss.
Case Study: The Parity Wallet Breach
In 2017, a vulnerability in the Parity multi-sig wallet led to the freezing of over $150 million worth of Ethereum. This incident highlighted the following points:- Code Audits: Regular and thorough code audits are essential, especially for smart contracts.
- User Awareness: Users need to be aware of the risks associated with using complex smart contracts and the importance of using audited and widely accepted solutions.
Case Study: MyEtherWallet DNS Hijacking
In 2018, MyEtherWallet (MEW), a popular Ethereum wallet, experienced a DNS hijacking attack. During this incident, users who attempted to access MEW were redirected to a phishing site, leading to the theft of around $150,000 worth of cryptocurrency. This case study provides critical insights into the importance of DNS security and user vigilance.- DNS Security: This attack highlighted the need for robust DNS security measures to prevent hijacking and ensure users are accessing legitimate websites.
- User Vigilance: Users must be vigilant about verifying URLs and using bookmarks to access wallet services to avoid falling victim to phishing sites.
- Security Practices: Implementing additional security practices such as 2FA and hardware wallets can mitigate the risks associated with DNS hijacking and phishing attacks.
Case Study: Fake Ledger Application on Official Microsoft App Store
In December 2022, the official Ledger support account on X (formerly known as Twitter) warned users about a fake ledger application that was published on Microsoft App Store as shown in the following picture.
Figure 2: The official Ledger support social media account warned users about a fake ledger application that was published on Microsoft App Store.
Source: https://cointelegraph.com/news/fake-ledger-live-app-sneaks-into-microsoft-app-store-as-victims-lose-half-a-million
In November 2023, a similar incident occurred involving a fake Ledger application on the Microsoft App Store. The total amount of stolen assets was roughly 16.8 BTC, worth around $588K at that time. This event underscored several key lessons:
- Security and Verification Procedures: App stores need robust security measures and verification procedures to prevent fake or malicious applications from being published. Microsoft, like other app stores, needs to continually refine its processes to detect and remove such applications promptly.
- User Education and Awareness: Users need to be educated about the risks of downloading applications from unofficial sources or trusting applications solely based on their appearance in an official app store. They should be encouraged to verify the legitimacy of applications and review permissions before installation.

Figure 3: A similar incident involving a fake Ledger application on the Microsoft App Store occurred in November 2023.
Source: https://cointelegraph.com/news/fake-ledger-live-app-sneaks-into-microsoft-app-store-as-victims-lose-half-a-million
Future Trends in Web3 Wallet Security
As technology advances, the security landscape for Web3 wallets is also evolving. Innovations such as multi-signature wallets, where multiple approvals are required for a transaction, and the integration of biometric authentication are emerging to enhance security. Additionally, decentralised identity solutions are being developed to reduce reliance on traditional authentication methods, further protecting user assets.Conclusion
Web3 wallets are a cornerstone of the decentralised digital ecosystem, providing users with autonomy over their digital assets. However, with this autonomy comes the responsibility to secure these assets against a myriad of threats. By understanding the types of wallets available, recognising potential security risks, and implementing best practices, users can significantly enhance the security of their Web3 wallets and protect their digital wealth in the decentralised world. As the Web3 space continues to grow, staying informed and vigilant will be key to navigating this new frontier safely.References
- https://github.com/slowmist/Blockchain-dark-forest-selfguard-handbook/blob/main/README.m
- https://www.quicknode.com/guides/web3-fundamentals-security/basics-to-web3-wallets
- https://slowmist.medium.com/beginners-guide-to-web3-security-navigating-wallet-types-and-risks-d7fd7b417f87
- https://cointelegraph.com/news/fake-ledger-live-app-sneaks-into-microsoft-app-store-as-victims-lose-half-a-million
- https://www.kaspersky.com/blog/fake-trezor-hardware-crypto-wallet/48155/

