In the ever-evolving landscape of software development, the importance of secure coding cannot be understated. Vulnerabilities in application can lead to dire consequences, including data loss, security breaches, and severe operational disruption. With cyber threats evolving rapidly, ensuring the security of applications has become more critical than ever. From mobile applications to web services and enterprise solutions, developers must adhere to secure coding practices to mitigate the risk of data breaches, unauthorised access, and other security vulnerabilities. This article delves into the principles and best practices of secure coding, aiming to provide developers with the knowledge to fortify their code against potential threats.
Understanding Secure Coding
Secure coding involves practices and methodologies that developers implement to write code that is free of vulnerabilities and defend against possible attacks. By understanding common vulnerabilities and their consequences, developers can implement proactive measures to safeguard their code against potential exploits. It's about building a solid foundation of security principles to create robust and reliable software systems.
Principles of Secure Coding and Best Practices
Understanding and applying these common principles is crucial for creating resilient code. In this section, we will delve into these principles:
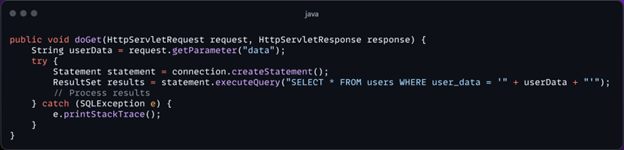
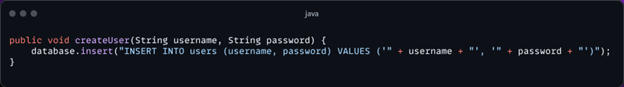
This code directly uses user input in a SQL query, which can lead to SQL Injection attacks if the input is not sanitised.
Secure Practice: Use prepared statements with parameterised queries:

By incorporating input validation and sanitisation, web applications can significantly reduce the risk of security vulnerabilities arising from malicious user input.
Vulnerable Code Example in Java:
Consider a web application with an authentication system. Suppose there's a function responsible for updating a user's email address:

This function updates a user's email address without checking whether the current user has the appropriate privileges to perform this action. Any authenticated user can potentially update any other user's email address.
Secure Practice: Ensure that functions operate with the minimal privileges necessary for their specific tasks. In this case, the function should first check if the current user has the authority to update the specified user's email address:

The updated code checks whether the current user is an admin or is the same user whose email is being updated. If either condition is met, the email update proceeds; otherwise, an UnauthorisedAccessException is thrown.
By following the Least Privilege Principle, this revised code ensures that only users with the necessary privileges can perform sensitive actions, mitigating the risk of unauthorised access and potential security breaches.
Vulnerable Code Example in Java:
Consider a web application with a login functionality that uses basic authentication:
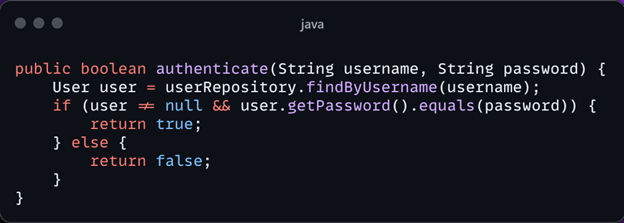
This authentication method is susceptible to various attacks, including brute force attacks and SQL injection, due to its vulnerability to password interception and user enumeration.
Secure Practices: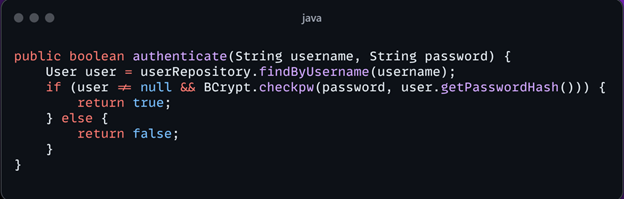
This revised code stores passwords securely using bcrypt hashing. When a user attempts to log in, their password is hashed and compared with the stored hash. This prevents the exposure of plain-text passwords even if the database is compromised.
Secure Authorisation:
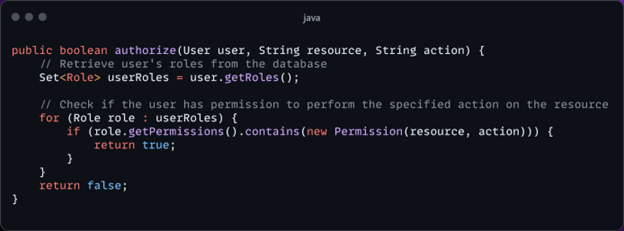
This method checks whether the user has the necessary permissions to perform a specific action on a resource. It iterates through the user's roles, checking if any of them include the required permission.
By implementing secure authentication and authorisation practices, web applications can ensure that only authenticated and authorised users access sensitive resources, reducing the risk of unauthorised access and data breaches.
Vulnerable Code Example in Java:
Consider a web application that stores user passwords in plain text:
Storing passwords in plain text leaves them vulnerable to theft if the database is compromised.
Secure Data Storage Practices
In this improved code, the BCryptPasswordEncoder is used to securely hash the password before storing it in the database. The hashed password is then inserted into the database using a parameterised query, preventing SQL injection attacks.
Secure Data Transmission Practices
Vulnerable Code Example in Java:
Consider a scenario where an error message exposes sensitive information:
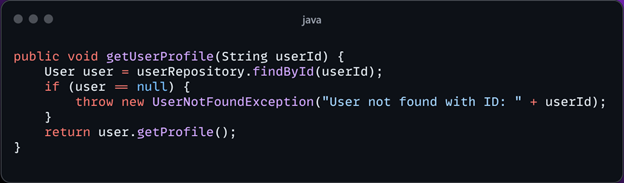
This code throws an exception containing the user ID, potentially exposing sensitive information to attackers.
Secure Error and Exception Handling Practices: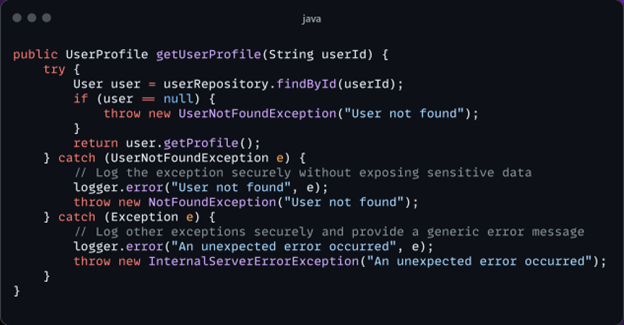
In this improved code, the method catches specific exceptions and provides generic error messages to users. It securely logs exceptions without exposing sensitive information. Different types of exceptions are handled appropriately, ensuring that users receive meaningful error messages while attackers gain minimal insight into system internals.
By implementing secure error and exception handling practices, web applications can maintain confidentiality, integrity, and availability while reducing the risk of exploitation by attackers.
Secure Configuration and Hardening Practices:
Tools for Secure Coding
In addition to understanding secure coding principles, developers can use various open-source or enterprise tools to enhance application security:
Using these tools helps developers identify and mitigate security risks efficiently. However, remember that tools should complement, not replace, a culture of security awareness and best practices within the development team.
Conclusion
Secure coding is a critical aspect of software development that requires ongoing effort and vigilance. By understanding common vulnerabilities, implementing secure coding practices, and regularly testing and monitoring your applications, you can significantly reduce the risk of security breaches and protect sensitive data. Remember, security is a shared responsibility, and every developer plays a crucial role in building secure software.
Understanding Secure Coding
Secure coding involves practices and methodologies that developers implement to write code that is free of vulnerabilities and defend against possible attacks. By understanding common vulnerabilities and their consequences, developers can implement proactive measures to safeguard their code against potential exploits. It's about building a solid foundation of security principles to create robust and reliable software systems.
Principles of Secure Coding and Best Practices
Understanding and applying these common principles is crucial for creating resilient code. In this section, we will delve into these principles:
- Input Validation and Sanitisation: Ensuring that all input received by the system is validated and sanitised to prevent common attacks like SQL injection and cross-site scripting.
- Least Privilege Principle: Granting the minimum level of access necessary for a particular function, thereby limiting the potential damage from a security breach.
- Secure Authentication and Authorisation: Implementing robust authentication and authorisation mechanisms to ensure that only legitimate users can access sensitive functions and data.
- Secure Data Storage and Transmission: Protecting data at rest and in transit with encryption and secure protocols to prevent unauthorised access and interception.
- Error and Exception Handling: Managing errors and exceptions in a way that does not expose sensitive information or system vulnerabilities.
- Secure Configuration and Hardening: Configuring systems and applications securely by default and hardening them against known attack vectors.
1. Input Validation and Sanitisation
Validating and sanitising user input is crucial for preventing attacks such as SQL injection, cross-site scripting (XSS), and other malicious input manipulations. Always ensure that the input conforms to expected formats and is safe to use in operations such as database queries.
Vulnerable Code Example in Java:
This code directly uses user input in a SQL query, which can lead to SQL Injection attacks if the input is not sanitised.
Secure Practice: Use prepared statements with parameterised queries:

By incorporating input validation and sanitisation, web applications can significantly reduce the risk of security vulnerabilities arising from malicious user input.
2. Least Privilege Principle
Vulnerable Code Example in Java:
Consider a web application with an authentication system. Suppose there's a function responsible for updating a user's email address:

This function updates a user's email address without checking whether the current user has the appropriate privileges to perform this action. Any authenticated user can potentially update any other user's email address.
Secure Practice: Ensure that functions operate with the minimal privileges necessary for their specific tasks. In this case, the function should first check if the current user has the authority to update the specified user's email address:

The updated code checks whether the current user is an admin or is the same user whose email is being updated. If either condition is met, the email update proceeds; otherwise, an UnauthorisedAccessException is thrown.
By following the Least Privilege Principle, this revised code ensures that only users with the necessary privileges can perform sensitive actions, mitigating the risk of unauthorised access and potential security breaches.
3. Secure Authentication and Authorisation
Vulnerable Code Example in Java:
Consider a web application with a login functionality that uses basic authentication:

This authentication method is susceptible to various attacks, including brute force attacks and SQL injection, due to its vulnerability to password interception and user enumeration.
Secure Practices:
- Use Strong Authentication Mechanisms: Implement multi-factor authentication (MFA) or OAuth for stronger user authentication. For example, using OAuth with providers like Google or Facebook can offload authentication responsibilities to trusted third parties.
- Encrypt Passwords: Store passwords securely using strong cryptographic hashing algorithms like bcrypt or Argon2. Salt the passwords to prevent rainbow table attacks.
- Prevent User Enumeration: Avoid providing distinct error messages for incorrect usernames and passwords to prevent attackers from determining valid usernames. Instead, provide generic error messages.
- Implement Role-Based Access Control (RBAC): Assign roles to users and grant permissions based on these roles. Ensure that users have access only to the resources they need to perform their tasks.

This revised code stores passwords securely using bcrypt hashing. When a user attempts to log in, their password is hashed and compared with the stored hash. This prevents the exposure of plain-text passwords even if the database is compromised.
Secure Authorisation:

This method checks whether the user has the necessary permissions to perform a specific action on a resource. It iterates through the user's roles, checking if any of them include the required permission.
By implementing secure authentication and authorisation practices, web applications can ensure that only authenticated and authorised users access sensitive resources, reducing the risk of unauthorised access and data breaches.
4. Secure Data Storage and Transmission
Vulnerable Code Example in Java:
Consider a web application that stores user passwords in plain text:

Storing passwords in plain text leaves them vulnerable to theft if the database is compromised.
Secure Data Storage Practices
- Hash Passwords: Store passwords securely by hashing them using a strong cryptographic hashing algorithm such as bcrypt or Argon2. This ensures that even if the database is compromised, the passwords remain protected.
- Use Salt: Apply a unique salt to each password before hashing to prevent attackers from using precomputed rainbow tables for password cracking.
- Encrypt Sensitive Data: Encrypt sensitive data such as user credentials, credit card details, and personally identifiable information (PII) before storing it in the database. Utilise strong encryption algorithms and securely manage encryption keys.
- Implement Access Controls: Enforce strict access controls to limit who can access sensitive data in the database. Use role-based access control (RBAC) to assign permissions based on user roles.

In this improved code, the BCryptPasswordEncoder is used to securely hash the password before storing it in the database. The hashed password is then inserted into the database using a parameterised query, preventing SQL injection attacks.
Secure Data Transmission Practices
- Use HTTPS: Encrypt data transmitted between the client and the server using HTTPS (HTTP over SSL/TLS) to prevent eavesdropping and tampering by attackers.
- Implement Secure Protocols: Use secure communication protocols like TLS (Transport Layer Security) for data transmission. Keep TLS configurations up to date to mitigate vulnerabilities.
- Avoid Transmitting Sensitive Data in URLs: Do not include sensitive information such as passwords or session IDs in URLs, as they can be easily intercepted and exposed.
- Validate SSL/TLS Certificates: Validate SSL/TLS certificates to ensure that communication is secure and prevent man-in-the-middle attacks.
5. Error and Exception Handling
Vulnerable Code Example in Java:
Consider a scenario where an error message exposes sensitive information:

This code throws an exception containing the user ID, potentially exposing sensitive information to attackers.
Secure Error and Exception Handling Practices:
- Use Generic Error Messages: Avoid providing detailed error messages to users or attackers. Instead, use generic messages that do not reveal internal system details.
- Log Errors Securely: Log errors and exceptions securely, ensuring that sensitive information is not included in log files. Utilise logging frameworks with proper configuration to mask or redact sensitive data.
- Handle Exceptions Gracefully: Catch exceptions at appropriate levels and handle them gracefully without revealing system details. Provide users with a generic error message and log the details for debugging purposes.
- Implement Rate Limiting: Implement rate limiting to prevent brute force attacks on error-prone endpoints. Limit the number of requests per IP address or user account within a specified time frame.

In this improved code, the method catches specific exceptions and provides generic error messages to users. It securely logs exceptions without exposing sensitive information. Different types of exceptions are handled appropriately, ensuring that users receive meaningful error messages while attackers gain minimal insight into system internals.
By implementing secure error and exception handling practices, web applications can maintain confidentiality, integrity, and availability while reducing the risk of exploitation by attackers.
6. Secure Configuration and Hardening
Secure Configuration and Hardening Practices:
- Default Security Settings: Configure systems and applications with security in mind from the beginning. Use secure default settings to minimise vulnerabilities.
- Regular Updates: Keep software up to date with the latest security patches. This closes known security holes and keeps your systems secure.
- Access Controls: Implement strict access controls to limit who can access what. This prevents unauthorised access to sensitive areas.
- Secure Authentication: Use strong authentication methods, like multi-factor authentication, to verify users' identities. This prevents unauthorised access, even if passwords are compromised.
- Network Segmentation: Divide your network into smaller, isolated segments to limit the impact of a security breach. This prevents attackers from moving freely within your network.
- Default Security Settings: Configure firewalls to block unnecessary ports by default.
- Regular Updates: Keep operating systems and software updated with the latest security patches.
- Access Controls: Restrict access to sensitive files to only authorised users.
- Secure Authentication: Implement multi-factor authentication for accessing critical systems.
- Network Segmentation: Use VLANs to separate guest networks from internal networks.
Tools for Secure Coding
In addition to understanding secure coding principles, developers can use various open-source or enterprise tools to enhance application security:
- Static Code Analysis Tools: Scan source code to find vulnerabilities. Examples: SonarQube, Semgrep, Brakeman, Bandit, etc.
- Dynamic Application Security Testing (DAST) Tools: Test running applications for vulnerabilities. Examples: Burp Suite, OWASP ZAP.
- Dependency Scanning Tools: Identify vulnerabilities in third-party dependencies. Examples: DependencyCheck, BlackDuck, Snyk, etc.
- Security Testing Frameworks: Provide structured security testing approaches. Examples: OWASP, MSTG.
- Security Training Platforms: Offer courses on secure coding practices. Examples: Cybrary, SANS Institute.
Using these tools helps developers identify and mitigate security risks efficiently. However, remember that tools should complement, not replace, a culture of security awareness and best practices within the development team.
Conclusion
Secure coding is a critical aspect of software development that requires ongoing effort and vigilance. By understanding common vulnerabilities, implementing secure coding practices, and regularly testing and monitoring your applications, you can significantly reduce the risk of security breaches and protect sensitive data. Remember, security is a shared responsibility, and every developer plays a crucial role in building secure software.
Addtional Resources and References:
- OWASP (Open Web Application Security Project): https://owasp.org/
- OWASP Secure Coding Practices-Quick Reference Guide: https://owasp.org/www-project-secure-coding-practices-quick-reference-guide/
- Secure Coding Practices: https://owasp.org/www-project-secure-coding-practices-quick-reference-guide/stable-en/02-checklist/05-checklist
- OWASP Secure Coding Dojo: https://owasp.org/www-project-secure-coding-dojo/
- SANS Institute: https://www.sans.org/
- Fortify: https://www.microfocus.com/en-us/products/static-code-analysis-sast/overview
- Checkmarx: https://www.checkmarx.com/
- SonarQube: https://www.sonarqube.org/
- Burp Suite: https://portswigger.net/burp
- OWASP ZAP: https://owasp.org/www-project-zap/
- Snyk: https://snyk.io/
- Nexus Lifecycle: https://www.sonatype.com/products/lifecycle
- Mobile Security Testing Guide (MSTG): https://mobile-security.gitbook.io/mstg/

