Introduction
Modern technologies frequently improve our lives, but they also create new opportunities for cybercriminals to violate our privacy and steal our identities. As Quick-Response (QR) codes gain popularity, cybercriminals are now exploiting them to carry out malicious activities.Invented in the 1990s, QR codes gained popularity during the pandemic. Since the COVID-19 pandemic, the adoption of QR code technology has grown as customers prefer contactless transactions. QR codes have been widely employed across various industries, from track-and-trace systems to ordering from menus at restaurants and making parking payments. However, as this technology has become more widespread, cybercriminals have increasingly targeted our growing familiarity with it.
QR codes can be easily scanned using smartphones, allowing consumers to access promotions, digital tickets, and other content simply by pointing their phone's camera at the code. However, not all QR Codes are legitimate.
Why are QR Code Attacks so attractive to cybercriminals?
The most common approaches threat actors use to exploit QR codes are:
- Embedding QR codes with malicious URLs.
- Replacing legitimate QR codes with compromised ones by simply pasting their QR codes over pre-existing ones.
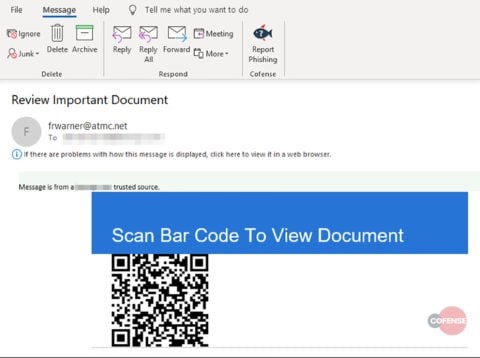
Figure 1: Example of a phishing email.
QR Code Attack Types
Threat actors use various lures and strategies to deceive users into scanning malicious QR codes, similar to phishing attacks. Common types of QR code attacks include:Clickjacking: One of the simplest QR code scams to execute is clickjacking. In some cases, individuals are paid to get others to click on specific links. A common approach involves replacing QR codes on well-known monuments, where people expect to receive background information about the landmark by scanning the QR code. Instead, the altered QR code directs users to a dubious website, where the clickjacking operator earns a fee.
Phishing (quishing): QR phishing, also known as quishing, involves tricking victims into scanning a malicious QR code that directs them to a fake website or downloads malware. QR codes often appear trustworthy when placed on brochures, advertisements, or products by shady actors imitating trustworthy businesses. When scanned by a smartphone camera, the malware executes without the user realising they have been redirected to a malicious site.
Malware attacks: Cybercriminals can use QR codes to lure unsuspecting individuals to sites that automatically download harmful malicious software onto their mobile devices. The malware can cause significant harm, including opening backdoors for additional malware infections or silently stealing the target's information and sending it to cybercriminals. In some cases, these malware infections may even involve ransomware attacks, holding the victim's information hostage until a ransom is paid.
QRLJacking: Quick Response code Login Jacking (QRLJacking) is a type of attack that targets QR code-based login systems. In this type of attack, the hacker replaces the service provider's QR code with a malicious one, enabling them to gain unauthorised control of the user's account. The user scans the hacker's QR code rather than the service provider's QR code, allowing the hacker to obtain control of the user account.
The QRLJacking attack works as follows:
- The attacker initiates a client-side QR session and replicates the login QR code to a phishing website. “A well-designed phishing page with an active, frequently updated QR code is prepared for distribution to the victim.”
- The attacker sends the phishing page to the victim.
- The victim uses a targeted mobile app to scan the QR code.
- The attacker takes over the victim's account.
- The service transfers all of the victim's data to the attacker during the attacker's session.
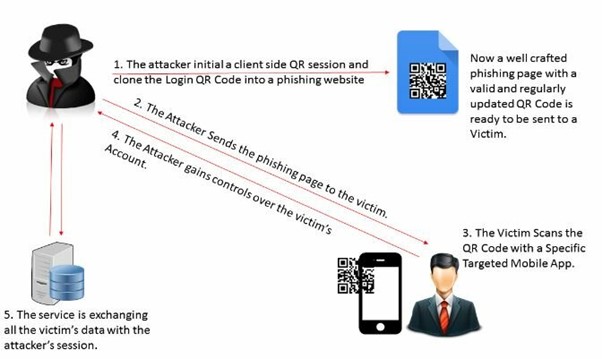
Figure 2: An illustration of how the QRLJacking attack works. (Source: https://owasp.org/www-community/attacks/Qrljacking)
QR Code Scams
Parking meter payment: Fraudulent QR codes are often placed on the back side of parking meters, leading victims to believe they may pay for parking using the QR code. After making payment via the QR code, some victims return to find their cars towed or receive a parking penalty. Additionally, their payment information is often collected for subsequent misuse.
Bank phishing scams: Bank branches frequently display notices on their front doors or easel placards with special promotions encouraging new account registration or use of additional services. Cybercriminals can easily replace the legitimate QR code with one that leads to their malicious website.
Cryptocurrency wallets: The rise of cryptocurrency has lured many people into transactions that are prime targets for scammers. Cryptocurrency trading, such as Bitcoin, occurs online, and QR codes are the most convenient way for both legitimate and fraudulent traders to direct investors to their digital wallets.
Romance scams: Some cybercriminals spend months developing an online romantic relationship with their victim, eventually offering financial advice or requesting financial assistance via a bitcoin exchange. The victim then uses the provided QR code to send the desired funds directly to the scammer's digital wallet.
Utility and government impostors: Cybercriminals frequently pose as representatives from utility companies, the Social Security Administration, or the Internal Revenue Service (IRS) regarding an overdue debt. The scammer claims that failure to pay may result in arrest, additional fines, or termination of access to electricity, gas, or water services. The cybercriminal may inform the victim that the usual payment portal for these services is currently unavailable, but payment can be made through another portal by following a link or scanning a QR code.
Recommendations and Mitigations
The top recommendation is to avoid using "Login with QR code" unless absolutely necessary. There are several solutions to mitigate this issue, and the following can be used together or independently:
- Session Confirmation: The most effective recommendation is to implement a confirmation message or notification that displays specific information about the client/server session.
- IP Restrictions: Restricting any authentication process over various wide-area networks (WANs) reduces the attack window.
- Location-based Constraints: Limiting authentication processes based on location reduces the attack window.
- Authentication by Sound: A potential solution is to incorporate a sound-based authentication step into the process. Technology exists that can create unique data, convert it to audio, and recognise it in its original form, making this approach feasible.
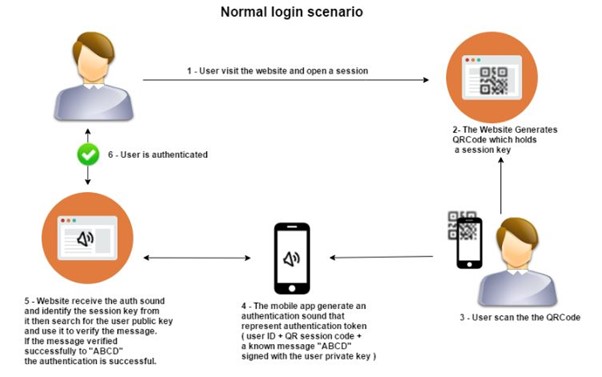
Figure 3: An illustration of the normal login process with QR code login and sound authentication. (Source: https://owasp.org/www-community/attacks/Qrljacking)
Attack Scenario (with Mitigation):
-
The attacker visits the website and initiates a session.
-
The website generates a QR code that contains a session key.
-
The attacker creates a phishing website using the received QR code and sends it to the user.
-
The user scans the attacker's QR code on the phishing page.
-
The mobile app generates an authentication sound and sends it to the phishing website.
-
The phishing website is unable to process and collect the authentication audio because it requires additional browser permissions.
-
Even if the attacker attempts to generate the authentication sound using the User ID, he still lacks the secret key.
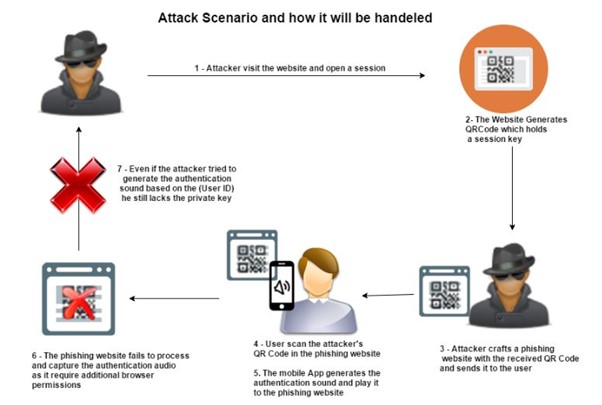
Figure 4: An illustration of the attack and mitigation scenario for the login process with QR code login and sound authentication. (Source: https://owasp.org/www-community/attacks/Qrljacking)
How to Protect Against QR Code Attacks
Individuals can protect themselves against QR code attacks by following these guidelines:
-
Avoid downloading apps from QR codes. Use your phone's app store for safer downloads.
-
When you scan a QR code, ensure the URL is correct and appears authentic. A malicious domain name may closely resemble the desired URL but contain typos or misplaced letters.
-
Avoid scanning QR codes in emails, particularly if they appear to be from organisations or individuals you know.
-
When scanning a physical QR code on a sign, window, or placard, ensure it is not superimposed.
-
If you receive a notification to complete a payment via QR code, contact or visit the company's website to confirm its legitimacy.
-
If you receive a QR code from someone you know, contact them using a known phone number or address to confirm that the code is genuine.
-
Install a mobile security app for virus and malware protection to keep your smartphone secure, or install a scam blocker or web filter on your device to safeguard against recognised scams.
Conclusion
To avoid falling victim to threats such as QRLJacking, organisations should consider implementing a confirmation message or notification for users that displays specific information about the session initiated by the client-server, as well as setting a time limit (typically within 3 minutes) to complete each login session. Limiting authentication processes to specific networks and/or locations will further reduce the attack surface. Organisations should also consider deploying mobile threat protection solutions on devices that have access to corporate apps and data. This will help identify and mitigate mobile attacks, including those involving malicious QR codes.References
- https://www.csa.gov.sg/Tips-Resource/publications/cybersense/2020/quick-response-code-related-cyber-threats
- https://owasp.org/www-community/attacks/Qrljacking
- https://www.infosecurity-magazine.com/opinions/qr-codes-vulnerability-cybercrimes
- https://www.alvareztg.com/fbi-warns-of-rising-qr-codes-attacks

