As organisations strive to build strong cybersecurity defences, many are quick to adopt advanced technologies such as artificial intelligence (AI)-driven threat detection, automation, and zero trust architectures. However, without a solid foundation, these sophisticated tools may fall short of their full potential or, even worse, obscure underlying security weaknesses.
Proactive and fundamental cybersecurity audits and vulnerability assessments are essential first steps in establishing that foundation. They provide organisations with a clear understanding of their current security posture, identify gaps in policies, procedures, and technical controls, and help prioritise risks based on actual exposure. By identifying and remediating basic vulnerabilities early on, businesses can reduce the risk of exploitation and avoid the costly consequences of security breaches.
Beginning with these essential assessments ensures that future cybersecurity investments are informed, strategic, and aligned with actual needs. This approach supports alignment with business goals, ensures ongoing regulatory compliance, and promotes a culture of continuous improvement.
In essence, before advancing to high-level security technologies or complex strategies, organisations must first understand and strengthen their cybersecurity fundamentals through regular and proactive audits and vulnerability assessments. This foundational step is critical for achieving effective, long-term cybersecurity resilience.
Understanding Cybersecurity Audits and Vulnerability Assessments
Cybersecurity audits and vulnerability assessments are fundamental components of a robust cybersecurity program. While they share the common goal of enhancing an organisation’s security posture, they differ in scope, approach, and outcomes.
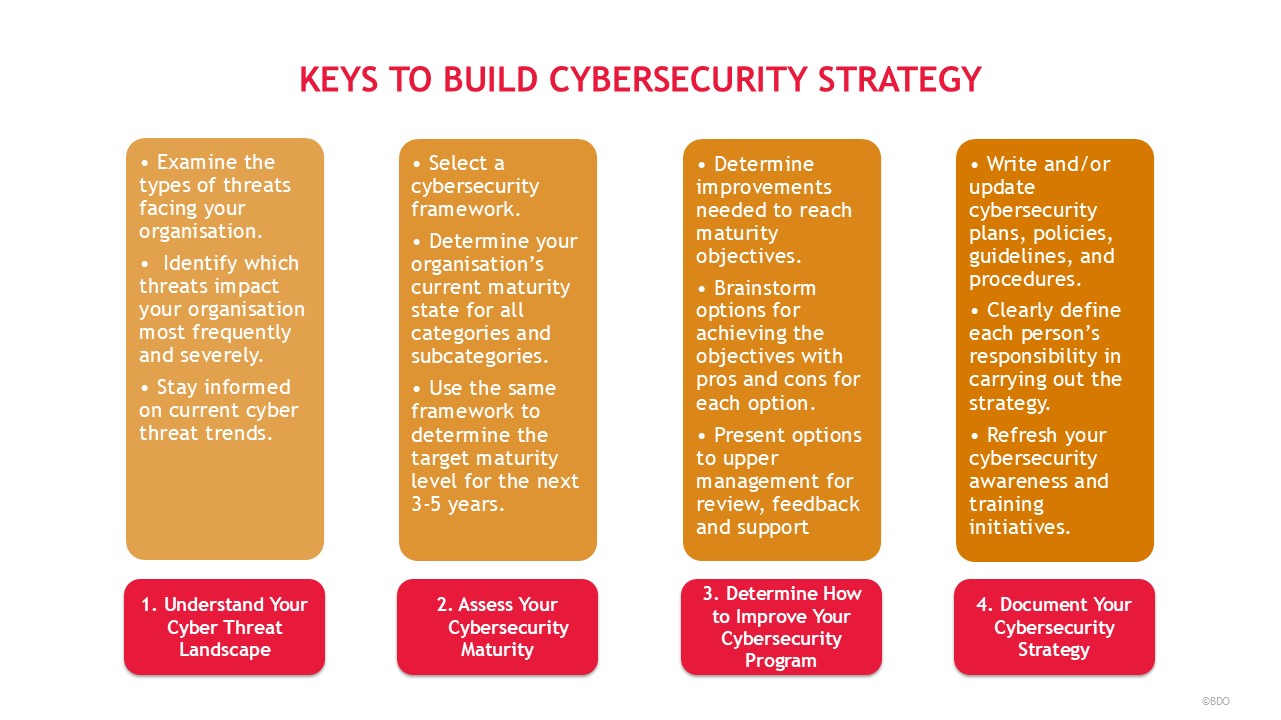
Figure 1: Keys to Build Cybersecurity Strategy
Cybersecurity Audits are comprehensive evaluations that review an organisation’s security policies, procedures, controls, and compliance with relevant laws and standards. These audits typically involve examining documentation, interviewing key personnel, and testing security controls to ensure they are effectively designed and implemented. Audits help identify gaps in governance, risk management, and operational security, providing management with insights into how well security objectives are being met.
Vulnerability Assessments, on the other hand, focus on identifying technical weaknesses within an organisation’s IT environment, such as software bugs, misconfigurations, or outdated systems that attackers could exploit. Using automated tools and manual testing techniques, vulnerability assessments scan networks, servers, applications, and endpoints to detect vulnerabilities. The findings are then prioritised based on risk, enabling IT teams to address the most critical issues promptly.
Together, these processes provide a proactive means to detect and remediate potential threats before they can be exploited by malicious actors. Understanding their distinct roles allows organisations to develop an integrated security strategy that balances compliance, risk reduction, and continuous improvement.
Why Organisations Must Prioritise Proactive Cybersecurity Audits and Vulnerability Assessments
In the current environment dominated by AI-driven threat detection, zero-trust models, and next-generation firewalls, many organisations prioritise investing in advanced cybersecurity technologies. Although these tools are essential, they are not infallible. Often overlooked yet vital are the foundational practices of performing ongoing cybersecurity audits and vulnerability assessments.
Why They Are Fundamental
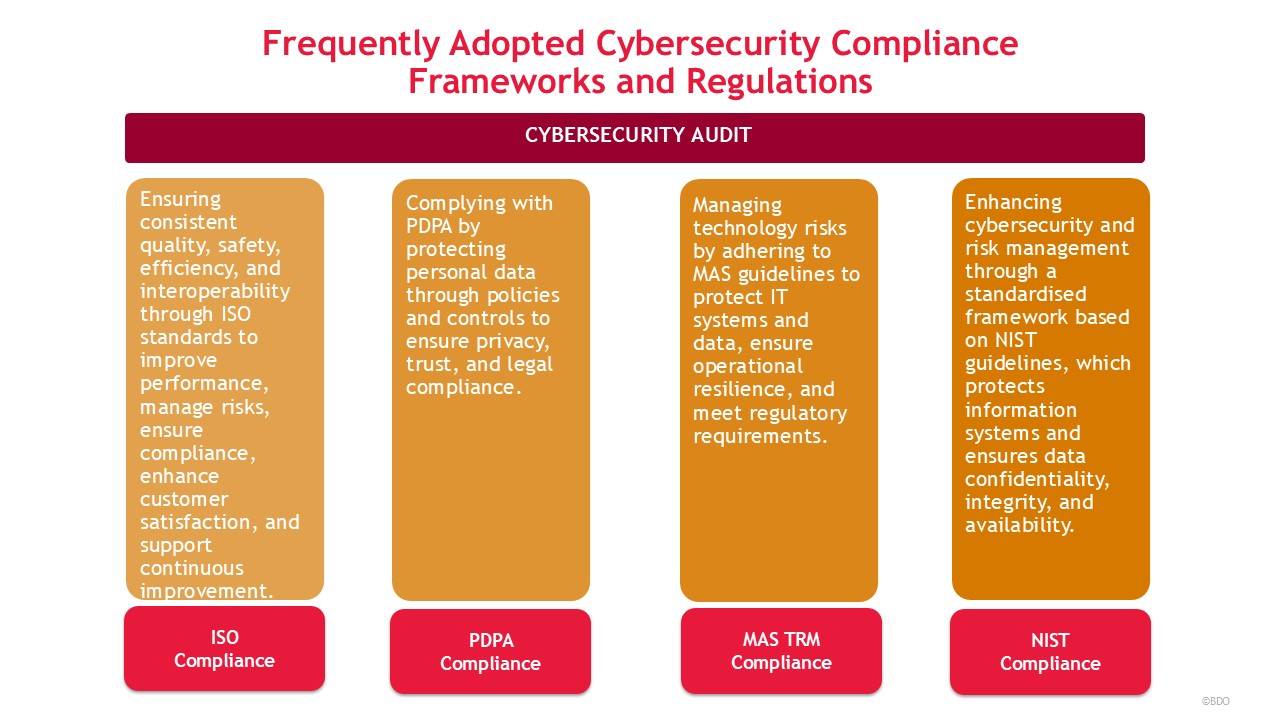
Figure 2: Frequently Adopted Cybersecurity Compliance Frameworks and Regulations
Why Organisations Overlook Them
Enhancing Cyber Resilience Through External Independent Cybersecurity Audits and Vulnerability Assessments
Engaging an external independent auditor to perform security assessments and vulnerability evaluations offers organisations several critical advantages that enhance both the effectiveness and credibility of their cybersecurity efforts:
Committing to these continuous and foundational processes is more than a best practice; it is a critical business necessity. BDO can help organisations establish and maintain these vital cybersecurity audits and vulnerability assessments, ensuring that your security measures are effective and that your environment remains resilient against evolving threats.
References
Proactive and fundamental cybersecurity audits and vulnerability assessments are essential first steps in establishing that foundation. They provide organisations with a clear understanding of their current security posture, identify gaps in policies, procedures, and technical controls, and help prioritise risks based on actual exposure. By identifying and remediating basic vulnerabilities early on, businesses can reduce the risk of exploitation and avoid the costly consequences of security breaches.
Beginning with these essential assessments ensures that future cybersecurity investments are informed, strategic, and aligned with actual needs. This approach supports alignment with business goals, ensures ongoing regulatory compliance, and promotes a culture of continuous improvement.
In essence, before advancing to high-level security technologies or complex strategies, organisations must first understand and strengthen their cybersecurity fundamentals through regular and proactive audits and vulnerability assessments. This foundational step is critical for achieving effective, long-term cybersecurity resilience.
Understanding Cybersecurity Audits and Vulnerability Assessments
Cybersecurity audits and vulnerability assessments are fundamental components of a robust cybersecurity program. While they share the common goal of enhancing an organisation’s security posture, they differ in scope, approach, and outcomes.

Figure 1: Keys to Build Cybersecurity Strategy
Cybersecurity Audits are comprehensive evaluations that review an organisation’s security policies, procedures, controls, and compliance with relevant laws and standards. These audits typically involve examining documentation, interviewing key personnel, and testing security controls to ensure they are effectively designed and implemented. Audits help identify gaps in governance, risk management, and operational security, providing management with insights into how well security objectives are being met.
Vulnerability Assessments, on the other hand, focus on identifying technical weaknesses within an organisation’s IT environment, such as software bugs, misconfigurations, or outdated systems that attackers could exploit. Using automated tools and manual testing techniques, vulnerability assessments scan networks, servers, applications, and endpoints to detect vulnerabilities. The findings are then prioritised based on risk, enabling IT teams to address the most critical issues promptly.
Together, these processes provide a proactive means to detect and remediate potential threats before they can be exploited by malicious actors. Understanding their distinct roles allows organisations to develop an integrated security strategy that balances compliance, risk reduction, and continuous improvement.
Why Organisations Must Prioritise Proactive Cybersecurity Audits and Vulnerability Assessments
In the current environment dominated by AI-driven threat detection, zero-trust models, and next-generation firewalls, many organisations prioritise investing in advanced cybersecurity technologies. Although these tools are essential, they are not infallible. Often overlooked yet vital are the foundational practices of performing ongoing cybersecurity audits and vulnerability assessments.
Why They Are Fundamental
- Proactive Risk Identification: While advanced detection tools often spot threats only after they have entered the environment, continuous audits and vulnerability assessments enable organisations to detect weaknesses and misconfigurations before attackers can exploit them. These processes reveal outdated systems, inadequate access controls, and ineffective policies —issues that even the most sophisticated detection tools cannot resolve on their own.
- Visibility Across the Entire Ecosystem: Vulnerability assessments and audits offer a holistic, full-circle view of systems, users, and processes. They ensure that every element, whether it be a third-party SaaS platform, an unmanaged endpoint, or a cloud instance—is evaluated against evolving threats and compliance standards.
- Alignment with Governance and Compliance: Security audits play a vital role in maintaining compliance with frameworks such as ISO 27001, CIS Controls, and NIST CSF, as well as regulatory requirements including PDPA, MAS TRM, GDPR, and HIPAA. While detection tools may overlook governance gaps, audits confirm that policies, procedures, and controls are properly implemented and enforced.

Figure 2: Frequently Adopted Cybersecurity Compliance Frameworks and Regulations
- Preventing "Security Drift": Over time, even well-configured environments can deteriorate because of system changes, human error, or lack of enforcement. Regular audits and assessments help prevent configuration drift, reinforce baseline security practices, and promote continuous improvement.
- Return on Investment (ROI): Identifying and mitigating vulnerabilities early, before they escalate into breaches, can save an organisation millions in potential losses. Continuous auditing ensures that existing investments, including advanced tools, are properly configured and delivering the value they were intended to provide.
Why Organisations Overlook Them
- False Sense of Security from Tools: Many businesses believe that deploying expensive SIEMs, EDRs, or AI-based detection platforms provides full protection. They often neglect the fact that detection is reactive, and without understanding their existing exposure, these tools may only alert once damage has already begun.
- Lack of Internal Expertise: Conducting effective vulnerability assessments and audits demands a combination of technical expertise and governance knowledge — skills which not all IT or security teams possess internally. Without the appropriate skills and personnel, these essential tasks are often deprioritised or carried out ineffectively, leaving organisations exposed to unnecessary risks.
- Budget Misalignment: Security budgets frequently prioritise visible and marketable solutions that promise immediate results. In contrast, audits and assessments, though less flashy, offer a much more fundamental foundation. Unfortunately, they are often overlooked during budget discussions.
- Assumption of One-Time Fixes: Some organisations view audits and assessments as one-time compliance requirements rather than ongoing processes. By taking this approach, they fail to keep up with the evolving nature of threats and changes within their systems.
Enhancing Cyber Resilience Through External Independent Cybersecurity Audits and Vulnerability Assessments
Engaging an external independent auditor to perform security assessments and vulnerability evaluations offers organisations several critical advantages that enhance both the effectiveness and credibility of their cybersecurity efforts:
- Objective and Unbiased Evaluation: External auditors bring an impartial perspective, free from internal biases or assumptions. They can identify weaknesses and risks that internal teams might overlook due to familiarity or organisational blind spots, ensuring a more thorough and honest assessment.
- Specialised Expertise and Experience: Independent auditors often possess deep technical knowledge and broad industry experience gained from working across multiple organisations and sectors. This expertise enables them to apply best practices, incorporate emerging threat intelligence, and leverage advanced assessment methodologies that may not be available in-house.
- Compliance and Regulatory Assurance: Many regulatory frameworks and industry standards require or recommend independent third-party assessments for compliance validation. External audits provide trusted evidence of compliance, which can simplify regulatory reporting, reduce penalties, and enhance stakeholder trust.
- Enhanced Credibility and Stakeholder Confidence: A report from a reputable external auditor carries more weight with customers, partners, investors, and regulators. It demonstrates the organisation's commitment to cybersecurity transparency and accountability, helping to build stronger business relationships and bolster brand reputation.
- Identification of Emerging Risks and Best Practices: External auditors stay current with the latest cyber threats, vulnerabilities, and mitigation techniques. They bring this knowledge into assessments, helping organisations anticipate new risks and adopt industry-leading security controls.
- Resource Optimisation: Leveraging external auditors allows internal IT and security teams to focus on core operational tasks and remediation efforts, while the auditors provide an independent evaluation. This improves overall efficiency and effectiveness of the security program.
- Benchmarking and Continuous Improvement: Third-party assessments often include benchmarking against industry standards or peers, enabling organisations to measure their security posture objectively and identify areas for ongoing improvement.
Conclusion
Advanced detection tools are valuable; however, without the essential foundation of ongoing cybersecurity audits and vulnerability assessments, they function in isolation. Creating a secure environment begins with understanding your assets, identifying what is vulnerable, and verifying that your defences are functioning correctly. Neglecting this crucial step is akin to setting up a cutting-edge security system in a building with unlocked doors and open entrances.Committing to these continuous and foundational processes is more than a best practice; it is a critical business necessity. BDO can help organisations establish and maintain these vital cybersecurity audits and vulnerability assessments, ensuring that your security measures are effective and that your environment remains resilient against evolving threats.
References
- What BDO can do for your business: https://www.bdo.com.sg/en-gb/services/advisory/cybersecurity
- BDO Strategic SOCaaS: https://www.bdo.com.sg/engb/services/advisory/digitalisation/bdo-strategic-socaas
- The Future of Cybersecurity Assessments Is Here: https://www.isaca.org/resources/isaca-journal/issues/2023/volume-2/the-future-of-cybersecurity-assessments-is-here
- What is Cyber Security Compliance?: https://www.trendmicro.com/en_no/what-is/governance-risk-management-and-compliance-grc/cyber-security-compliance.html
- Enhanced Cyber Trust (2025) – Covers classical cybersecurity, cloud security, OT security and AI security: https://www.csa.gov.sg/our-programmes/support-for-enterprises/sg-cyber-safe-programme/cybersecurity-certification-for-organisations/cyber-trust/certification-for-the-cyber-trust-mark
- Vulnerability Assessment: 6 Best Steps to Better Security: https://egs.eccouncil.org/wp-content/uploads/2020/12/Risk-and-Vulnerability-Assessment-Do-You-Know-the-Other-Side.pdf

