The world of Web3, with its promise of Decentralised finance (DeFi) and permissionless innovation, represents a new frontier for investors. However, this landscape is also fraught with peril, chief among them the pervasive threat of the "rug pull." The scale of this problem is staggering; in 2021 alone, rug pulls siphoned over $2.8 billion from unsuspecting investors1. These scams are particularly rampant in the less regulated and hype-driven corners of the ecosystem, such as DeFi, non-fungible tokens (NFTs), and memecoins, where projects can materialise and attract capital with breathtaking speed.
A rug pull is a malicious exit scam where the creators of a cryptocurrency project abruptly abandon their project, absconding with all the invested capital and leaving participants with worthless digital tokens. The term is derived from the idiom of "pulling the rug out" from under investors' feet, causing a sudden and catastrophic collapse in value. While the Web3 space presents these unique risks, investors are not powerless. It is possible to significantly mitigate exposure to rug pulls by adopting a rigorous, multi-layered due diligence framework. This framework combines fundamental project analysis, quantitative on-chain investigation, and a healthy dose of skepticism, empowering investors to navigate the trustless environment with confidence.
Section 1: The Anatomy of a Rug Pull
To effectively combat rug pulls, one must first understand their mechanics. These scams are not monolithic, they exist on a spectrum of deceit and are executed through various methods, each with its own tell-tale signs.
1.1 The Spectrum of Deceit: Hard vs. Soft Rug Pulls
Rug pulls can be broadly categorised into two types: hard and soft. The distinction lies in the intent, legality, and execution speed of the scam.
Hard Rug Pulls are premeditated, malicious, and illegal acts of fraud. In these scenarios, developers harbour the intent to defraud investors from the project's inception. They achieve this by embedding malicious code such as backdoors, infinite minting functions, or code that prevents selling directly into the project's smart contracts2. The exit is swift and absolute. The project's website, social media accounts, and all communication channels vanish without a trace, leaving investors with no recourse and worthless assets. Because these actions involve explicit deception and theft, they can often be prosecuted under existing financial crime statutes for wire fraud and money laundering. The successful prosecution of the founders of the Frosties NFT project, who were charged with exactly these crimes, serves as a prominent example.
Soft Rug Pulls represent a more insidious and legally ambiguous form of exit scam. This method involves a gradual abandonment of the project rather than an abrupt theft. Developers, who may have initially had legitimate intentions, slowly and quietly sell off their substantial holdings of the project's token. This sustained selling pressure inevitably causes the token's price to plummet, eroding investor value over time. Concurrently, the team reduces their involvement, halting development updates and communication with the community. While deeply unethical, this "slow fade" approach provides perpetrators with plausible deniability. They can attribute the project's demise to market forces, technical challenges, or a strategic pivot, making it far more difficult to prove criminal intent compared to the clear-cut theft of a hard rug pull.
1.2 Common Execution Methods
Scammers employ several well-established techniques to execute both hard and soft rug pulls.
Liquidity Stealing: This is the quintessential hard rug pull and the most common method seen in the DeFi space. The process is deceptively simple. Developers launch a new token and create a liquidity pool on a Decentralised Exchange (DEX) like Uniswap or PancakeSwap. They pair their new, worthless token with a cryptocurrency of established value, such as Ethereum (ETH) or Binance Coin (BNB). They then promote the project to attract investors, who swap their valuable ETH or BNB for the new token, thus adding to the liquidity pool. Once a substantial amount of capital has been accumulated, the developers then withdraw all the valuable cryptocurrency from the pool, instantly renders the token worthless, crashing its value to zero3. The AnubisDAO scam, which saw perpetrators vanish with nearly $60 million, is a textbook example of this technique.
Malicious Smart Contract Functions (Honeypots): This is a more technical type of hard pull where the trap is written directly into the code. A common variant is limiting sell orders, where the smart contract is coded to allow users to buy a token but explicitly prevents them from selling it. Often, only specific wallets whitelisted by the developers are permitted to sell. This creates what is known as a "honeypot": a trap that is easy to enter but impossible to leave. This mechanism guarantees a one-way flow of funds into the project. Scammers can then artificially inflate the price, sell their own holdings without issue, and disappear, leaving all other investors trapped with unsellable, worthless assets. In 2021, the infamous Squid Game (SQUID) token effectively utilised this method to defraud investors.
Dumping (Pump-and-Dump): This technique is the primary engine of soft rug pulls and is analogous to classic penny stock manipulation schemes. Developers and insiders often allocate a disproportionately large share of the token supply to themselves during the project's launch. They then orchestrate aggressive marketing campaigns, leveraging social media hype and unrealistic promises to create fear of missing out (FOMO) and artificially inflate—or "pump"—the token's price. Once the price reaches a desirable peak, these insiders "dump" their massive holdings onto the open market in a cascade of sell orders. The sudden influx of supply overwhelms demand, causing the price to collapse and leaving investors who bought in during the hype with devastating losses4. In February 2025, the LIBRA token was promoted on social media by Argentinian President Javier Milei. This high-level endorsement fuelled a speculative frenzy. However, insiders controlled an estimated 82% of the token supply and proceeded to cash out over $107 million5, causing the token's value to crash by 95% within hours and wiping out over billions in loses.
Section 2: The Due Diligence Framework: A Multi-Layered Vetting Protocol
Given the sophistication of these scams, investors require a systematic and comprehensive framework for evaluating new projects. Effective due diligence rests on four interconnected pillars: analysing the project and its team, decoding marketing and community signals, scrutinising the economic blueprint, and verifying technical integrity.
2.1 Project and Team Analysis
The foundation of any legitimate project is the credibility of its creators and the clarity of its vision.
-
Anonymous Teams: Legitimate projects are typically proud to showcase their teams, providing public, verifiable identities, active LinkedIn profiles, and a documented history of experience in blockchain technology or a relevant industry. Anonymity is the scammer's greatest tool, as it erases all accountability and facilitates a clean getaway. Investors must diligently research the team, verifying credentials and watching for red flags like AI-generated profile pictures or fake social media accounts. A prudent rule of thumb is: "No face, no funds".
-
The Whitepaper and Roadmap: A credible project is supported by a detailed and professional whitepaper6. This document should clearly articulate the problem the project aims to solve, the technology it employs, its specific use case, and a realistic, milestone-driven roadmap for future development. Warning signs include whitepapers that are vague, poorly written, filled with grammatical errors, overly reliant on buzzwords without substance, or, in some cases, directly plagiarised from other projects. The roadmap should present an achievable plan, not a series of ambitious goals that are perpetually "coming soon".
2.2 Marketing and Community Analysis
Scammers are masters of psychological manipulation, creating an illusion of value and urgency where none exists.
-
Unrealistic Promises and Guaranteed Returns: Any project that promises or guarantees high returns, especially in a short timeframe (e.g., "100x potential," "risk-free investment"), is almost certainly fraudulent7. The cryptocurrency market is inherently volatile, and no legitimate project can guarantee profits. Such claims are bait designed to lure in unsuspecting victims.
-
High-Pressure Tactics and FOMO: Malicious actors frequently employ high-pressure sales tactics to rush investors into making impulsive decisions without proper research. Phrases such as "Presale ends in 2 hours!" are engineered to trigger a Fear of Missing Out (FOMO). Unsolicited contact via direct messages on platforms like X, Discord, or Telegram offering "exclusive deals" is another hallmark of a scam.
-
Fake Community and Social Media Engagement: A strong, active, and engaged community is often a sign of a healthy project. A project with 100,000 followers but only a handful of likes and comments per post is highly suspicious. Investors should be wary of community channels on Discord or Telegram where critical questions or negative comments are systematically deleted, as this indicates censorship and a desire to hide flaws.
-
False Endorsements: Scammers often fabricate endorsements from celebrities or well-known companies to lend their project an air of legitimacy8. These are easily faked by simply placing a logo on a website. Investors should never take such claims at face value and must independently verify any partnership or endorsement through official announcements from the supposed partner or credible news outlets.
2.3 Tokenomics and Supply Distribution Analysis
The economic structure of a token, or its tokenomics, can reveal a developer's intentions and expose built-in mechanisms for a rug pull.
-
No Locked Liquidity: This is one of the most critical technical red flags in the DeFi space. To build trust, legitimate projects lock the majority of their initial liquidity pool tokens in a time-locked smart contract. This action, facilitated by services like UNCX Network, or Team Finance, prevents developers from withdrawing the funds prematurely. A project with no locked liquidity, or a lock that lasts for only a very short period, presents an open invitation for developers to drain the pool at any time9.
-
Concentrated Token Ownership: The distribution of a project's tokens should be reasonably Decentralised. If a small number of wallets control a significant portion of the total supply, it poses a severe risk. This concentration gives a few individuals, often the developers themselves, the power to manipulate the market or crash the price by dumping their holdings. A common guideline suggests that if the top ten wallets hold more than 20% of the total supply, it warrants extreme caution.
-
Unlimited Supply and Inflationary Models: A token with no hard cap on its total supply is susceptible to hyperinflation. Developers could potentially mint an infinite number of new tokens, diluting the value of all existing tokens and effectively stealing value from investors. While some projects have legitimate inflationary models, the mechanics should be transparent, predictable, and designed for ecosystem health, not developer enrichment.
-
Vesting Schedules: Tokens allocated to the project team and early private investors should be subject to a vesting schedule10. This means the tokens are released gradually over a set period (e.g., monthly over two years) rather than all at once. The absence of a vesting schedule is a major red flag, as it allows insiders to sell their entire allocation on the first day of public trading, crashing the price for retail investors.
2.4 Smart Contract Integrity Analysis
The smart contract is the heart of any Web3 project, and its integrity is paramount.
-
No Third-Party Security Audit: A security audit is a non-negotiable requirement for any project handling user funds. Reputable projects voluntarily submit their smart contract code to established security firms for a thorough review. These audits identify vulnerabilities, bugs, and potential exploits. The absence of a publicly available audit report is a giant red flag, suggesting the team is either not serious about security or is actively hiding malicious code.
-
Unverified Contracts: A project's smart contract source code should be publicly available and verified on a block explorer like Etherscan. Verification means that the deployed bytecode on the blockchain matches the human-readable source code provided by the developers. An unverified contract prevents the public and security researchers from inspecting the code, effectively hiding what it is programmed to do.
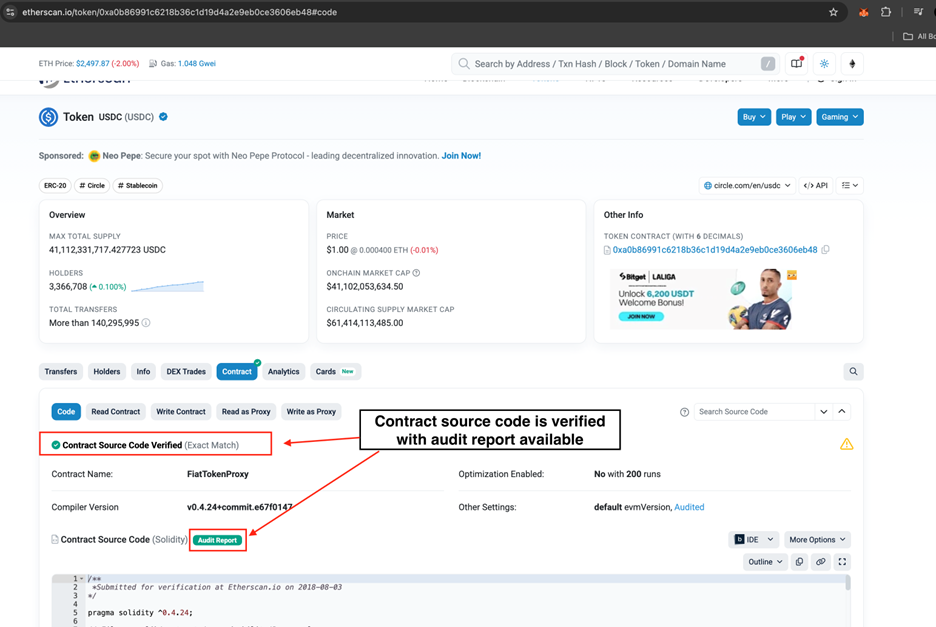 Figure 1: USDC Token Contract in Etherscan Explorer
Figure 1: USDC Token Contract in Etherscan Explorer
|
Category |
Checklist Item |
|
Team & Project |
Is the team public and verifiable? |
|
Team & Project |
Does the whitepaper clearly define utility and a realistic roadmap? |
|
Marketing & Community |
Are returns promised or guaranteed? |
|
Marketing & Community |
Are high-pressure sales tactics or FOMO being used? |
|
Marketing & Community |
Is community engagement genuine or botted/censored? |
|
Marketing & Community |
Are endorsements from reputable sources independently verifiable? |
|
Tokenomics |
Is a significant portion of liquidity locked for a long duration? |
|
Tokenomics |
Is token ownership Decentralised (not concentrated in a few wallets)? |
|
Tokenomics |
Is the total token supply capped? |
|
Tokenomics |
Do team and insider tokens have a clear vesting schedule? |
|
Technical Security |
Is a public audit report available? |
|
Technical Security |
Is the smart contract source code verified on a block explorer? |
Table 1: Cryptocurrency Project Due Diligence Checklist.
Section 3: The Investor's Toolkit: Practical Analysis for Rug Pull Detection
Theoretical knowledge of red flags must be paired with the practical skills to use investigative tools. This section provides hands-on guidance for conducting technical due diligence.
3.1 Using Block Explorers for On-Chain Forensics
Block explorers like Etherscan (for Ethereum), BscScan (for BNB Chain), and Solana Beach (for Solana Chain) are the public windows into the blockchain. They are the ultimate source of on-chain truth, allowing any user to verify transactions, inspect smart contracts, and track the flow of funds, all in real-time.
-
Investigating Holder Distribution: One of the first steps is to analyse who owns the token. By pasting the token's contract address into the explorer's search bar and navigating to the "Holders" or "Token Holders" tab, an investor can see a list of all wallets holding the token, ranked by the size of their holdings. A major red flag is high concentration, where a few wallets at the top of the list control a large percentage of the total supply. This indicates a high risk of a coordinated dump.
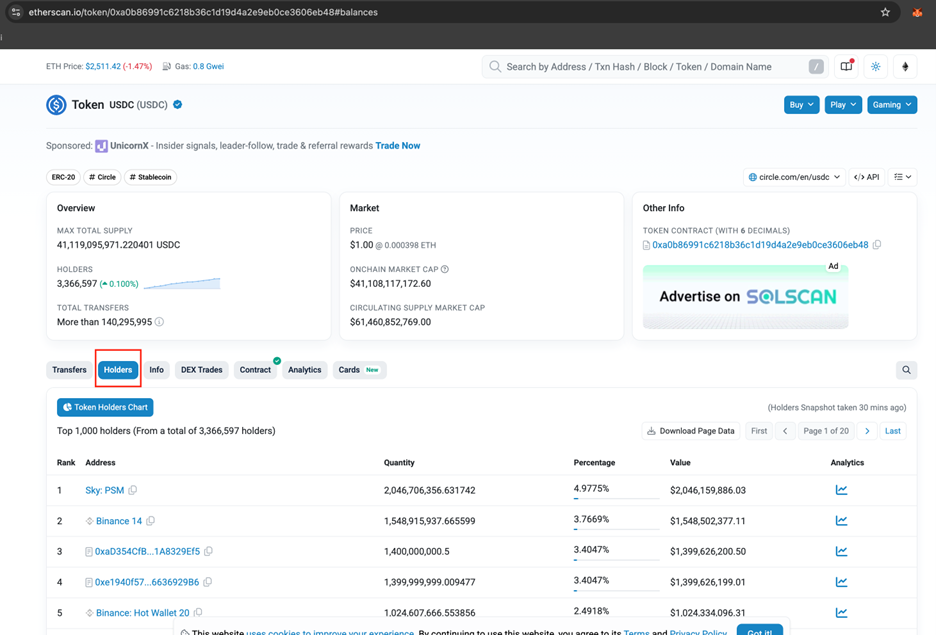 Figure 2: Holders Tab in Etherscan Blockchain Explorer.
Figure 2: Holders Tab in Etherscan Blockchain Explorer.
-
Analysing Liquidity Pool Transactions: For DeFi tokens, the liquidity pool is the project's lifeblood. On the explorer, an investor can find the address of the liquidity pool contract associated with the token. By examining its transaction history, one can see the initial liquidity provision (usually by the contract creator) and, crucially, any subsequent withdrawals of Liquidity Provider (LP) tokens. A large, sudden withdrawal of LP tokens by the creator's wallet is the definitive sign of a liquidity-stealing rug pull in progress.
-
Scrutinising the Contract Creator's Wallet: The wallet that deployed the smart contract is a key point of investigation. This address can be found on the main contract page in the explorer. Analysing this wallet's transaction history can reveal suspicious activities, such as large, early transfers of the new token to a handful of other wallets. This could indicate the pre-positioning of funds for a synchronised dump or the siphoning of project assets.
3.2 Leveraging Automated Detection Platforms
For investors who may lack deep technical expertise, several platforms have emerged that automate the process of risk assessment.
-
Overview of Token Scanners: Tools like Token Sniffer, De.Fi Scanner, and DexTools serve as valuable first-pass screening mechanisms11. They ingest a token's contract address and run a series of automated checks to generate a risk score or summary.
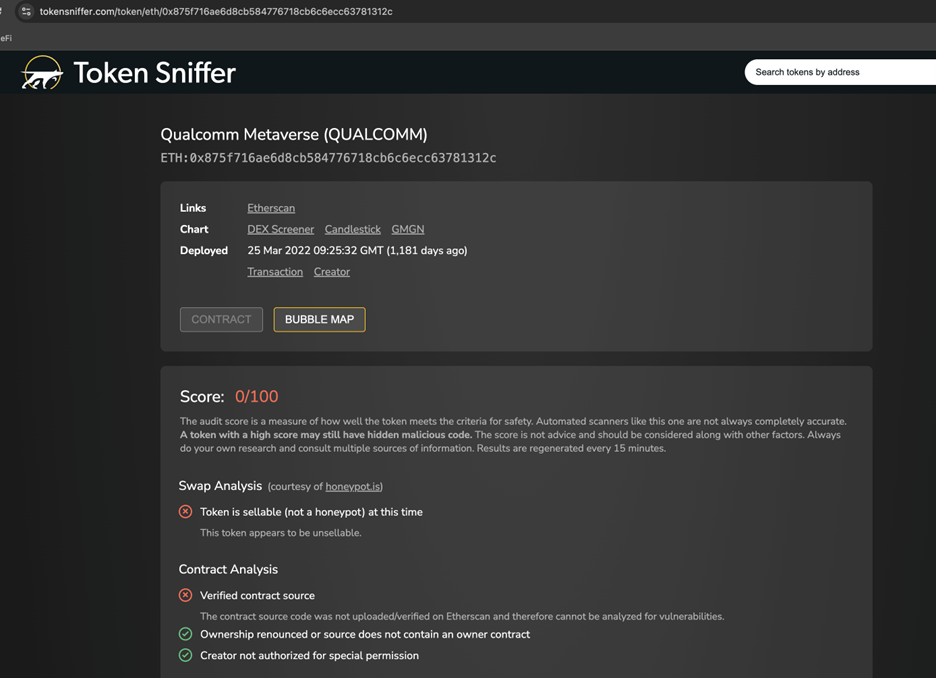 Figure 3: Token Sniffer detected that QUALCOMM token is unsellable.
Figure 3: Token Sniffer detected that QUALCOMM token is unsellable.
-
How They Work: These platforms automatically scan a smart contract's code for known vulnerabilities, such as honeypot functions that prevent selling. They also perform on-chain analysis to check for essential safety features, such as whether a sufficient portion of the liquidity is locked and whether the contract ownership has been renounced (meaning the developers can no longer modify it).
-
Limitations: It is crucial to understand that these automated tools are not infallible. They can sometimes produce false positives; for example, a scanner might flag a contract for having a "mint" function, even if that function has been permanently disabled by the developers. Therefore, these tools should be used as a starting point to identify potential red flags for deeper investigation, not as a definitive verdict. The block explorer always remains the ultimate source of ground truth.
Conclusion
The prevalence of rug pulls in the Web3 space represents a significant challenge to investor confidence and the maturation of the ecosystem. The financial losses are substantial, and the methods employed by scammers are constantly evolving in sophistication. However, the risk of falling victim to these schemes is not a foregone conclusion. A disciplined and multi-faceted approach to due diligence can dramatically reduce an investor's exposure to fraud.
The core principles for safe investing are clear. First is the necessity of a multi-layered vetting protocol that examines a project from every angle: the credibility of its team, the authenticity of its marketing, the soundness of its tokenomics, and the integrity of its code. Second is the importance of combining qualitative fundamental analysis with quantitative technical investigation, using tools like block explorers and automated detection platforms to verify claims and scrutinise on-chain activity. Finally, the entire process must be underpinned by a healthy and unwavering skepticism. Promises that seem too good to be true invariably are.
By internalising this framework, investors can shift from a position of vulnerability to one of empowerment. The tools and information needed to identify red flags are largely public and accessible. The power to prevent the success of rug pulls ultimately lies not with a single entity, but in the collective and individual commitment of market participants to conduct rigorous, evidence-based research. Through diligence, continuous learning, and a cautious mindset, investors can confidently navigate the risks of the trustless frontier and participate in the future of finance.
References
-
https://flipster.io/en/blog/rug-pulls-explained-how-to-spot-a-crypto-scam-before-its-too-late
-
https://adguard.com/en/blog/what-is-a-rug-pull-in-crypto.html
-
https://cointelegraph.com/news/argentine-prosecutor-aims-freeze-assets-libra-memecoin-fraud-case
-
https://neptunemutual.com/blog/how-to-spot-and-avoid-crypto-rug-pull-projects/
-
https://www.flowspecialty.com/blog-post/rug-pull-schemes-anatomy-of-a-digital-heist
-
https://help.1inch.io/en/articles/5363502-6-tools-to-identify-a-defi-scam-token

