Introduction
[19-20 October 2023] Singapore. Marina Bay Sands (MBS):Unauthorised intrusion into MBS systems resulted in the personal data of approximately 665, 000 non-casino rewards program members to be exposed1.
[26 December 2024] Japan. Japan Airlines (JAL):
Distributed denial of service (DDoS) attack caused 6 hours of flight cancellations and delays to domestic and international flights operated by JAL2,3.
These cases are but just two of the reported cybercrime incidents in the past 2 years.
What is Cybercrime?
Cybercrime refers to any criminal activity that causes harm to an individual, ranging from stealing personal information, to disrupting critical infrastructure using a computer, network or networked device.At present, there is no international consensus on what constitutes cybercrime4. “Cybercrime” is used as an umbrella term for online illegal activities that can be classified into two categories – cyber-dependent crimes, and cyber-enabled crimes.
In Singapore, the Singapore Police Force (SPF) defines these two categories as follows:
- Cyber-dependent crime: Offences under the Computer Misuse Act (CMA) in which the computer is a target. This includes offences such as ransomware, hacking and website defacements.
- Cyber-enabled crime: Offences in which the computer is used to facilitate the commission of an offence. Examples of cyber-enabled crime include online scams and cyber extortion, and other Penal Code offences committed via an online medium.
Is Cybercrime a Growing Concern?
Spurred by movement restriction measures during the COVID-19 pandemic, individuals and organisations have increasingly transitioned to managing both lifestyles and business processes digitally—a trend that has continued post-pandemic. Activities such as ordering meals and groceries, using work process tools to track deliveries and project completion status have required the sharing of sensitive data with third-party service providers, including digital platforms, cloud service providers, and other technology-related intermediaries. This increased connectivity has led to a proliferation of connected devices (including those powered by artificial intelligence (AI), Internet of Things (IoT)/Internet of Robotic Things-enabled devices) within both the office and residential networks. While the use of technology has significantly benefited our work and daily lives, it has also created a plethora of opportunities for cybercriminals to execute attacks such as ransomware, malware, phishing, data breaches, and distributed denial-of-service (DDoS) attacks on our devices and systems. In this article, we will focus on discussing ransomware and data breaches.1. Ransomware
Ransomware attacks are disruptive. At the organisational level, organisations often fall prey to ransomware due to failure to properly patch work devices, networks, and/or systems. When an organisation is hit by a ransomware attack, its data is encrypted by cybercriminals and rendered inaccessible. Victims, ranging from small enterprises to multi-national companies, often face operational disruptions5,6, such as system downtime and supply chain disruptions, as well as project delays until the ransom—often demanded in cryptocurrency—is paid. However, the challenges do not end there. Victims may also have to deal with data recovery, loss of customer trust7, negative publicity and legal issues.
Mr. Ivo Peixinho, head of Interpol’s Cybercrime Intelligence Unit, who spoke at the ISC2 Secure Asia Pacific conference at the Marina Bay Sands8, highlighted that ransomware attacks primarily target money-related sectors such as professional services, information technology, manufacturing and construction. However, he also noted a shift in attacks towards the critical infrastructure, with healthcare being a significant target. He emphasised that ransomware is not only capable of performing remote attacks that cause disruption to operations but also has physical consequences. He cited the tragic case of a woman who died due to delayed hospital admission in Germany following a ransomware attack that caused IT system failures.
The trend of double extortion attacks is now on the rise. According to the Singapore Cyber Landscape 2023 report9, two broad trends emerged in 2023:
- The shift towards exfiltration-only data extortion attacks by ransomware groups
- The additional pressure tactics to compel victims to pay ransom, such as threatening to report the victims to the authorities for their data breach unless a ransom is paid.

Figure 1: Frequency and key types of cybersecurity incidents encountered by organisations in Singapore. Source: Singapore Cybersecurity Health Report 2023 (https://www.csa.gov.sg/docs/default-source/our-programmes/support-for-enterprises/sg-cyber-safe-programme/csa-singapore-cybersecurity-health-report-2023.pdf?sfvrsn=c611e1b_1)
2. Data Breach
Data breaches can have far-reaching negative ripple effects on both individuals and organisations.
Individuals whose personal information has been compromised by data breach may become victims of identity theft, where cybercriminals use stolen identities to open accounts, make fraudulent purchases, or apply for loans in the victim’s name. Such fraudulent activities and unauthorised charges incurred can result in significant financial losses and emotional distress for the victims.
Organisations with compromised sensitive data due to a data breach may either be unaware of the breach or may have suffered the breach as a compounding effect of other cybercrimes, such as ransomware attacks. In the latter case, organisations may incur financial losses by paying a ransom to the cybercriminals to retrieve their data and hopefully, stop its proliferation and sale on the black market. Even if the affected organisations choose not to pay the ransom, they still face operational disruptions, system and data recovery costs, and any legal and regulatory fines imposed by regulatory bodies under frameworks such as the Personal Data and Protection Act (PDPA), and the General Data Protection Regulation (GDPR). Organisations will also have to pay higher insurance premiums to cover for their cyber risks. In addition to the reputational damage caused by the bad publicity and loss of consumer trust, organisations may also lose trade secrets and research data due to the data breach.
The need for robust data protection is a global concern. According to the 2024 Verizon Data Breach Investigations Report12, a regional analysis of cybercrime trends revealed that credentials accounted for a significant portion of compromised data in the APAC region (69%), while personal data comprised most compromised data in the EMEA and NA regions, at 64% and 50%, respectively.
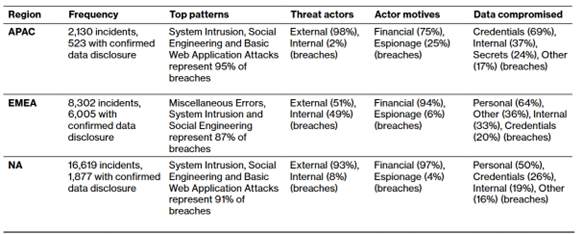
Legend:
- APAC: Asia and the Pacific, including Southern Asia, South-eastern Asia, Central Asia, Eastern Asia and Oceania.
- EMEA: Europe, Middle East and Africa, including Northern Africa, Europe and Eastern Europe, and Western Asia.
- NA: Northern America, which primarily consists of breaches in the United States and Canada.
In Singapore, the Singapore Cyber Landscape 2023 report9 noted a significant increase in data breach cases over the past three years, with the private sector accounting for a 22% rise in reported incidents. Additionally, 25% of reported data breach cases were attributed to cyber-attacks stemming from ransomware and phishing. Therefore, it is crucial for individuals and organisations to adopt a comprehensive and proactive approach to strengthen their cybersecurity posture to protect themselves from falling victim to cybercrime.
What are Some of the Initiatives the Global Community Has Taken to Disrupt Cybercrime?
1. World Economic Forum (WEF)
Cybercrime has been on the rise. The World Economic Forum (WEF) believes that collaboration among cybercrime investigators, national and international law enforcement agencies, and global businesses is the key in the fight against cybercrime. To this end, WEF launched the Partnership Against Cybercrime (PAC)13 initiative to bring global businesses, leading national and international law enforcement agencies, and leading not-for-profit organisations together, to address the global challenges of public-private cooperation in combating cybercrime.
WEF also launched the Cybercrime Atlas14 in 2023 to foster collaboration to improve the understanding of cybercriminal ecosystems by mapping the cybercrime landscape, operations, networks and infrastructure. By providing actionable research to the community and facilitating knowledge sharing among key stakeholders, it aims to address the evolving cyber threat landscape to combat cybercrime.
2. INTERPOL
International law enforcement agencies, like INTERPOL, play a crucial role in coordinating investigations and sharing intelligence across borders. To support global communities, INTERPOL has developed seven Global Policing Goals (GPGs) to address a range of crime and security issues. The seven GPGs were last reviewed in 2023 as part of a collaborative process led by INTERPOL, with input from regional law enforcement agencies worldwide, to ensure they align with the evolving security landscape.
INTERPOL’s Seven Global Policing Goals15:
- Goal 1: Enable the global law enforcement community to more effectively counter and prevent terrorism through international cooperation
- Goal 2: Promote border security worldwide
- Goal 3: Enhance the law enforcement response to protecting vulnerable communities
- Goal 4: Reduce the global harm and impact of cybercrime
- Goal 5: Tackle corruption and financial crime in all its forms
- Goal 6: Counter serious organised crime and drug trafficking
- Goal 7: Strengthen environmental security and support the promotion of sustainable livelihoods by countering crimes that affect the environment and climate
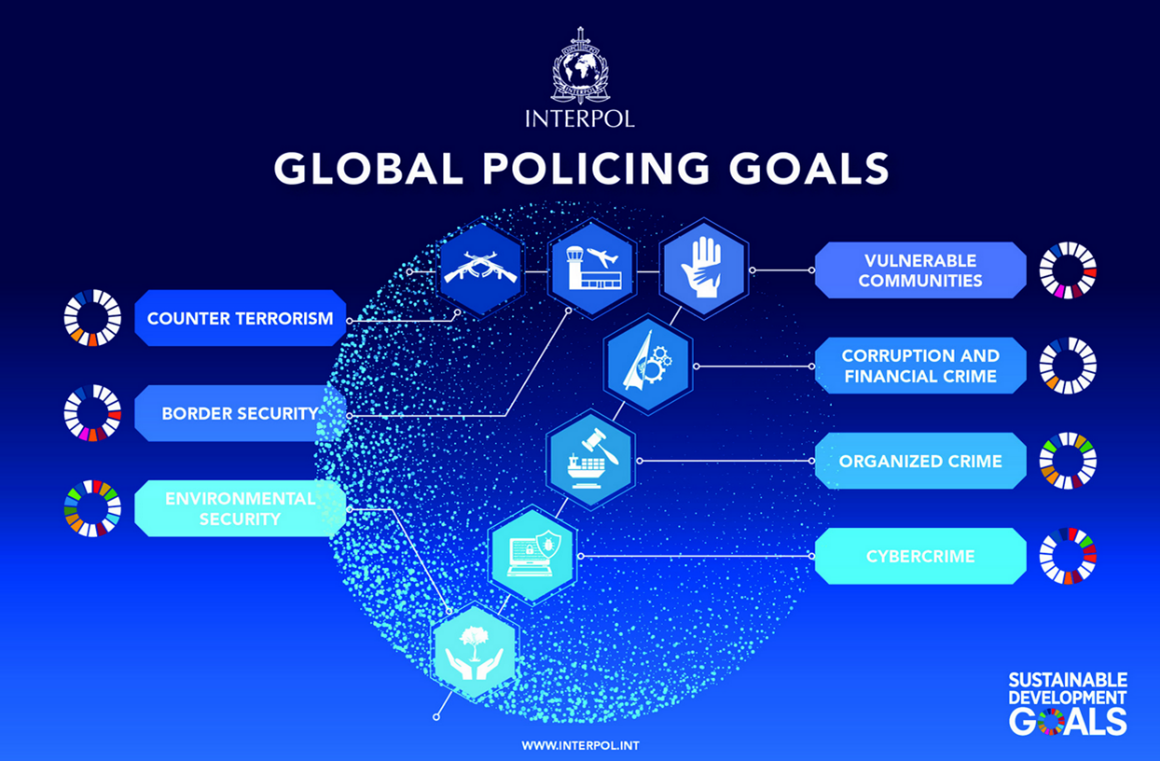 Figure 2: The 7 Global Policing Goals of INTERPOL. Source: https://www.interpol.int/en/Who-we-are/Strategy/Global-Policing-Goals
Figure 2: The 7 Global Policing Goals of INTERPOL. Source: https://www.interpol.int/en/Who-we-are/Strategy/Global-Policing-Goals3. Budapest Convention on Cybercrime
Nations have been working towards developing and implementing international treaties and agreements to tackle cybercrime, such as the Budapest Convention on Cybercrime, which is open for accession by any country.
The Budapest Convention on Cybercrime serves as a guideline for countries to establish domestic legislation on cybercrime and as a framework to enable practitioners to cooperate internationally.
According to the Budapest Convention16, it provides:
- The criminalisation of conduct for activities ranging from illegal access, data and systems interference to computer-related fraud and child pornography.
- Procedural powers to enable investigation of cybercrime and secure electronic evidence in relation to any crime.
- For efficient international cooperation to facilitate collaboration among nations to address cybercrime effectively.
4. The UN Convention against Cybercrime
The Convention serves three main purposes17:
- To promote and strengthen measures to prevent and combat cybercrime more efficiently and effectively.
- To promote, facilitate, and strengthen international cooperation in preventing and combating cybercrime.
- To promote, facilitate, and support technical assistance and capacity-building efforts to prevent and combat cybercrime, particularly for the benefit of developing countries.
- The Convention as a new tool for the growing threat of cybercrime.
- Facilitating round-the-clock protection through access to a 24/7 network by state parties.
- Protecting children by criminalising offences related to online child sexual abuse or exploitation material.
- Responding to victims’ needs in accordance with domestic law.
- Improving prevention through measures developed by state parties to reduce and manage the risks and threats of cybercrime.
What has Singapore Done to Help Local Enterprises and Organisations Disrupt Cybercrime?
More and more organisations in Singapore leverage emerging technologies, such as generative artificial intelligence (AI), to remain competitive both locally and globally. As the usage of emerging technologies grows, the sophistication and nature of cybercrimes evolved as well. For example, the number of AI-generated cyberattacks and instances of cybercriminals leveraging generative AI to carry out social engineering attacks or to spread disinformation has increased. As such, Singapore tackles cybercrime on multiple fronts.The Cyber Security Agency of Singapore (CSA) was established to protect Singapore’s cyberspace. The CSA continuously monitors the cyberspace for cyber threats and takes appropriate actions to mitigate the risks posed by these threats.
It launched the Singapore Cybersecurity Strategy19 to review its goals and approach for maintaining a safe cyberspace and to refresh its strategy to address new and emerging cyber threats. CSA also collaborates closely with industry players and academia, including institutes of higher learning and researchers from the National Cybersecurity Research and Development Programme (NCRP)20, to build a robust cybersecurity ecosystem and workforce.
As Singapore depends heavily on its critical information infrastructure (CIIs) to deliver essential services such as telecommunications, energy, transport, banking and finance, and healthcare, the following initiatives have been introduced to strengthen the cybersecurity and resilience of CIIs:
- Cybersecurity Act21: The Cybersecurity Bill, passed on 5 February 2018 and amended in May 2024, reflects changes in the cyber threat landscape. The four key objectives of the Cybersecurity Act are:
- Strengthening the protection of Critical Information Infrastructure (CII) against cyberattacks.
- Authorising CSA to prevent and respond to cybersecurity threats and incidents.
- Establishing a framework for sharing cybersecurity information.
- Establishing a light-touch licensing framework for cybersecurity service providers.
- Guidelines and Companion Guide on Security AI Systems22: The aim of the Guidelines and Companion Guide on Security AI Systems is to help system owners in using AI to manage cybersecurity risks such as supply chain attacks and adversarial machine learning.
- National Quantum-Safe Network Plus (NQSN+)23: The NQSN+ was introduced in 2023 to support network operators in deploying quantum-safe networks nationwide. Businesses working with NQSN+ operators can access quantum-safe networks to safeguard their critical data.
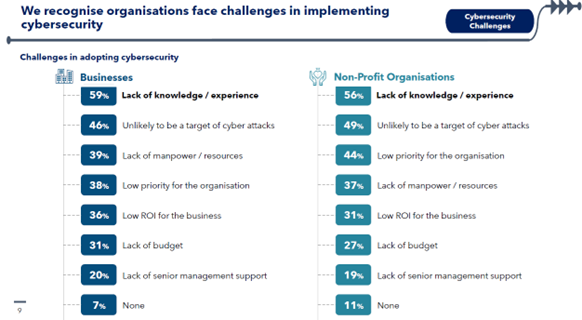
Figure 3: The challenges faced by businesses and non-profit organisations in implementing cybersecurity. Source: Singapore Cyber Security Health Report 2023 (https://www.csa.gov.sg/docs/default-source/our-programmes/support-for-enterprises/sg-cyber-safe-programme/csa-singapore-cybersecurity-health-report-2023.pdf?sfvrsn=c611e1b_1)
The CSA recognised this need, and thus introduced various initiatives to help local organisations and enterprises improve their cybersecurity posture. These initiatives include:
- Measure your cybersecurity health index: Organisations can use the Cybersecurity Health Check tool24 to identify gaps in their cyber hygiene and track their cybersecurity health.
- Implement Cyber Essentials / Cyber Trust: The Cyber Essentials25 mark is a cybersecurity certification designed for Small and Medium Enterprises (SMEs) looking to enforce good cyber hygiene and protect against common cyberattacks. The Cyber Trust26 mark is a cybersecurity certification for larger or more digitalised organisations with established cybersecurity experts, tools and resources in place to implement good cybersecurity practices aligned with their cybersecurity risk profiles.
- Utilise the CISO as-a-Service: Organisations that need assistance in implementing or developing robust cybersecurity practices and plans can leverage the CISO as-a-Service27.
- Use self-help resource, Internet Hygiene Portal28: Organisations can use this Internet Hygiene Portal for an overview of their internet hygiene. It allows organisations to assess the security of their websites, email services, and domain configurations, while offering recommended actions to improve their internet security posture.
- Tap on the Cybersecurity Labelling Scheme (CLS)29: CSA launched this CLS to enhance the security of Internet of Things (IoT) devices. With the increasing reliance on IoT devices such as Wi-Fi routers, Internet Protocol (IP) cameras, smart lights, and smart switches in homes, businesses, and critical infrastructure, compromised devices present a growing risk30. The CLS helps consumers make informed decisions when purchasing IoT devices. Notably, the CLS is now mutually recognised by countries like Finland and Germany.
- Leverage The AI Verify Foundation31: This was established to foster a community focused on enabling, testing, and governing the responsible use of AI. The open-source Testing Framework and Toolkit allows businesses to assess their AI systems against internationally recognised principles, such as those from the EU, OECD and Singapore.
What has Singapore Done to Enhance International Cyber Cooperation?
Singapore plays an active role in facilitating the sharing of threat intelligence and best practices across borders, enhancing international cyber cooperation and operational readiness with international organisations and other countries to combat cybercrime by:- Holding bilateral cyber dialogues with the United Kingdom (UK) and Malaysia in June and July 2024 respectively.
- Hosting a delegation from the Cyberspace Administration of China in July 2024.
- Hosting the 3rd US-Singapore Cyber Dialogue in October 2024.
- Chairing the United Nations Open-Ended Working Group on Security of and in the use of Information and Communications Technologies (2021-2025).
- Fostering cooperation on rules and norms, confidence-building measures, and capacity-building by convening the annual ASEAN Ministerial Conference on Cybersecurity.
- As the ASEAN Voluntary Lead Shepherd on Cybercrime, Singapore has led several initiatives to enhance regional cybersecurity cooperation such as, convening the 9th ASEAN Senior Officials' Roundtable on Cybercrime in October 2023 and the ASEAN Plus Three Cybercrime Conference in November 2023. These events aimed to strengthen collaboration among ASEAN member states and improve the region's collective response to cyber threats.
- The ASEAN Defense Ministers’ Meeting Cybersecurity and Information Centre of Excellence (ACICE) was established in June 2021 to foster collaboration among ASEAN member states in defense cybersecurity through information sharing and capacity building efforts. To further this objective, ACICE co-organised the 2nd Digital Defense Symposium in July 2024 with the S. Rajaratnam School of International Studies (RSIS) to address challenges related to digitalisation and modern warfare.
- Since 2022, the Singapore Government and the UK Home Office co-led the Policy Pillar under the International Counter Ransomware Initiative. This collaboration focuses on disrupting the ransomware ecosystem by developing and implementing strategies to counter threats posed by criminal ransomware groups.
Conclusion
The rapid rise of digitalisation, fueled by advancements in technologies like Artificial Intelligence (AI) and the Internet of Things (IoT), has significantly increased the complexity of the cyber threat landscape. This borderless environment necessitates a proactive approach to address digital risks. As supply chains increasingly integrate technology, they become more vulnerable to cyberattacks, particularly those reliant on technology providers and third parties.To combat these evolving threats, organisations and governments must continuously adapt their defense strategies. This requires active participation in initiatives led by governments and the global community to stay informed about the latest cybersecurity advancements and best practices. Ultimately, a collective effort involving individuals, organisations, and governments is crucial to disrupt cybercrime.
References
- https://www.straitstimes.com/tech/data-leak-hits-665000-mbs-rewards-programme-members
- https://www.forbes.com/sites/daveywinder/2024/12/26/hack-attack-against-japan-airlines-strikes-december-26-what-we-know/
- https://www.straitstimes.com/asia/east-asia/japan-airlines-hit-by-cyberattack-causing-some-delays-to-its-flights
- https://unu.edu/cpr/blog-post/understanding-uns-new-international-treaty-fight-cybercrime
- https://www.reuters.com/technology/cybersecurity/icbc-paid-ransom-after-hack-that-disrupted-markets-cybercriminals-say-2023-11-13/
- https://gfmag.com/banking/icbc-industrial-and-commercial-bank-of-china-ransomware/
- https://www.reuters.com/technology/cybersecurity/icbc-partners-wary-resume-trading-with-bank-after-cyberattack-bloomberg-news-2023-11-22/
- https://www.straitstimes.com/singapore/courts-crime/criminals-shifting-focus-to-target-healthcare-infrastructure-for-ransomware-attacks-interpol
- https://www.csa.gov.sg/docs/default-source/publications/2024/singapore-cyber-landscape-2023.pdf?sfvrsn=474022db_1
- https://www.channelnewsasia.com/singapore/shook-lin-and-bok-akira-ransomware-paid-ransom-bitcoin-4308441
- https://www.csa.gov.sg/docs/default-source/our-programmes/support-for-enterprises/sg-cyber-safe-programme/csa-singapore-cybersecurity-health-report-2023.pdf?sfvrsn=c611e1b_1
- https://www.verizon.com/business/resources/T307/reports/2024-dbir-data-breach-investigations-report.pdf
- https://www.weforum.org/projects/partnership-against-cybercime/
- https://initiatives.weforum.org/cybercrime-atlas/home
- https://www.interpol.int/en/Who-we-are/Strategy/Global-Policing-Goals
- https://rm.coe.int/cyber-buda-benefits-2024-july-2789-5929-5498-v-1/1680b0d659
- https://documents.un.org/doc/undoc/gen/n24/372/04/pdf/n2437204.pdf
- https://www.unodc.org/unodc/en/press/releases/2024/December/un-general-assembly-adopts-landmark-convention-on-cybercrime.html
- https://www.csa.gov.sg/Tips-Resource/publications/2021/singapore-cybersecurity-strategy-2021
- https://www.csa.gov.sg/News-Events/Press-Releases/2023/csa-establishes-cybersg-r-d-programme-office-with-four-year-funding-of-62-million-to-drive-research-and-development-to-build-up-cybersecurity-capabilities-in-singapore
- https://www.csa.gov.sg/legislation/Cybersecurity-Act
- https://www.csa.gov.sg/Tips-Resource/publications/2024/guidelines-on-securing-ai
- https://www.imda.gov.sg/about-imda/emerging-technologies-and-research/national-quantum-safe-network-plus
- https://services2.imda.gov.sg/CTOaaS/CyberHealthCheckCSA
- https://www.csa.gov.sg/our-programmes/support-for-enterprises/sg-cyber-safe-programme/cybersecurity-certification-scheme-for-organisation/cyber-essentials
- https://www.csa.gov.sg/our-programmes/support-for-enterprises/sg-cyber-safe-programme/cybersecurity-certification-scheme-for-organisation/cyber-trust
- https://www.csa.gov.sg/our-programmes/support-for-enterprises/sg-cyber-safe-programme/cybersecurity-certification-scheme-for-organisation/cybersecurity-health-plan
- https://www.csa.gov.sg/Tips-Resource/internet-hygiene-portal/
- https://www.csa.gov.sg/our-programmes/certification-and-labelling-schemes/cybersecurity-labelling-scheme
- https://www.straitstimes.com/tech/tech-news/strong-appetite-in-singapore-for-secure-smart-devices-survey-finds
- https://www.imda.gov.sg/resources/press-releases-factsheets-and-speeches/press-releases/2023/singapore-launches-ai-verify-foundation

