Introduction: A Strategic Shift in Cybersecurity
The Cybersecurity Maturity Model Certification (CMMC) represents a shift in how the U.S. Department of Defence approaches cybersecurity in its supply chain. As of 16 December 2024, this comprehensive framework has become mandatory for defence contractors, marking a significant evolution in the government's strategy to combat Advanced Persistent Threats (APTs) within the defence industrial base.This transformation shows that traditional compliance approaches often proved insufficient against determined adversaries, necessitating a more rigorous and verifiable approach to cybersecurity, and that self-attested compliance is sometimes not enough.
The Rationale Behind CMMC
CMMC emerged as a direct response to escalating cybersecurity threats targeting the defence supply chain and defence industrial base. Its primary objective is to ensure that contractors handling Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) implement security controls capable of dealing with the risks posed by sophisticated adversaries like nation-state actors.
This framework represents a fundamental shift from self-certification to third-party verification. The Department of Defence (DoD)'s decision to mandate CMMC reflects a growing understanding that cybersecurity is no longer only an IT concern, but a critical component of national security.
The Three-Tiered CMMC Model
The CMMC model establishes a 3-tiered approach to cybersecurity maturity, comprising distinct levels that reflect increasing sophistication in security practices:
- Level 1: At its foundation, Level 1 focuses on protecting FCI and implements basic safeguarding requirements from FAR 52.204-21. These fundamental security practices are essential for all contractors and establish the baseline for participation in the defence supply chain.
- Level 2: Moving up, Level 2 focuses on protecting CUI and incorporates all National Institute of Standards and Technology (NIST) SP 800-171 requirements. This intermediate level mandates documented security practices and regular security assessments, demonstrating a higher level of organisational commitment to cybersecurity.
- Level 3: At the pinnacle of the framework, Level 3 includes enhanced security requirements from NIST SP 800-172, featuring DoD-approved parameters for critical programs.
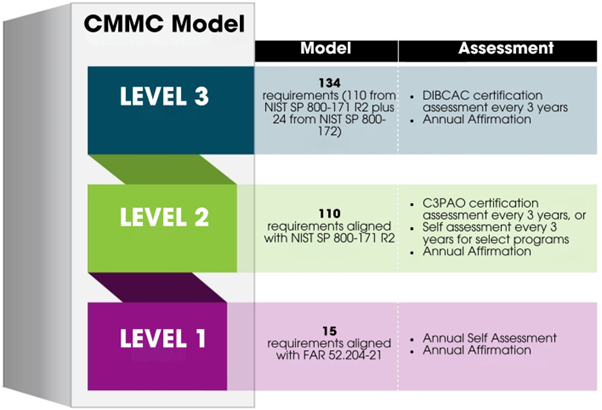
Figure 1: CMMC Levels 1 to 3. Source: https://dodcio.defense.gov/CMMC/About/
Phased Implementation Strategy
To ensure successful integration across the defence industrial base, the DoD has adopted a carefully planned four-phase implementation approach:
- Phase 1: Phase 1 begins immediately after the Defence Federal Acquisition Regulation Supplement (DFARS) revision, requiring Level 1 or Level 2 self-assessments for all applicable DoD solicitations and contracts. During this initial phase, contractors may opt for Certified Third-Party Assessor Organisation (C3PAO) certification for Level 2 assessments, demonstrating early commitment to enhanced security standards.
- Phase 2: Phase 2 introduces mandatory Level 2 certification assessment (C3PAO) for all applicable solicitations and contracts, beginning one calendar year after Phase 1's initiation. This marks a critical transition point where self-assessment alone becomes insufficient for high-risk contracts.
- Phase 3: This strategic rollout continues through Phase 3, where Level 2 certification becomes mandatory for all applicable contracts, and Level 3 requirements begin appearing in solicitations.
- Phase 4: Finally, Phase 4 marks full implementation across all contracts, including options on previously awarded contracts.
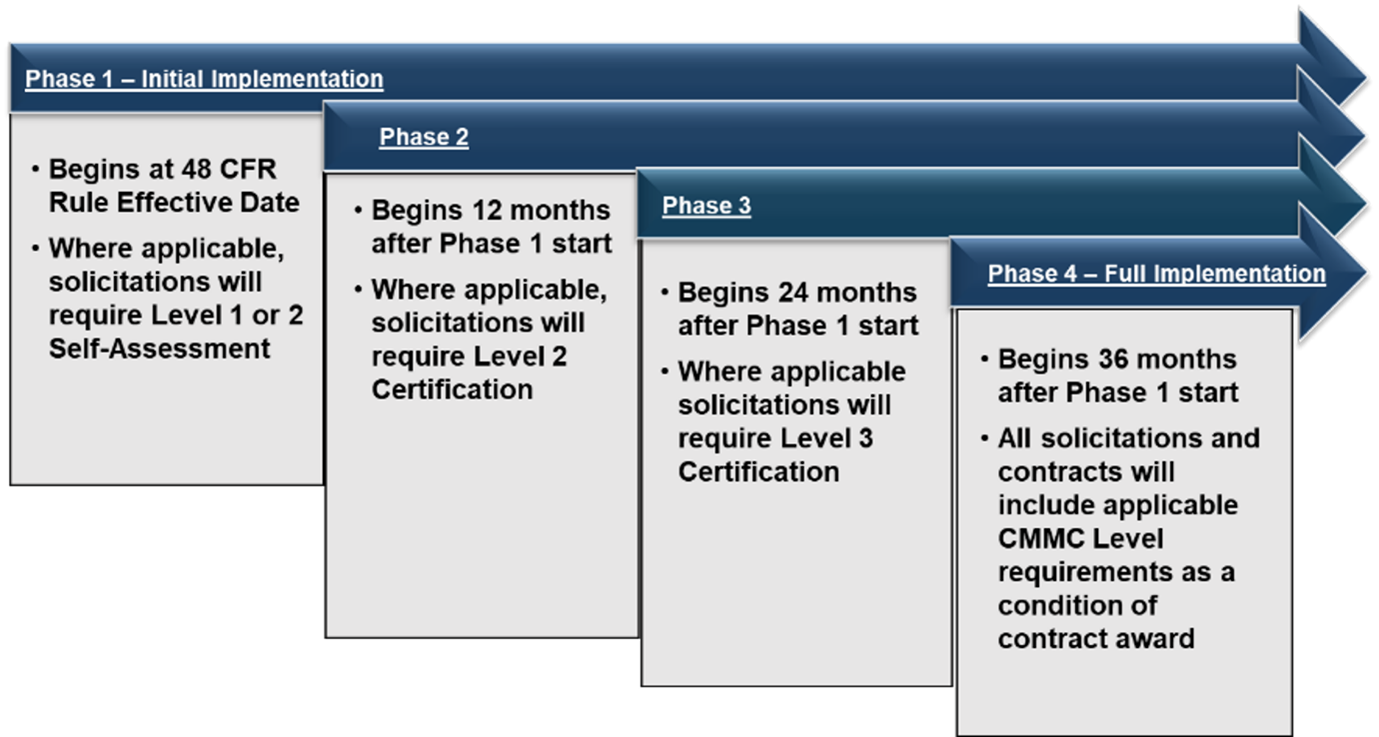
Figure 2: CMMC Phases 1 to 4. Source: https://dodcio.defense.gov/Portals/0/Images/CMMC/CMMC-Diagram.png
Organisational and Operational Implications
The operational implications of CMMC implementation are far-reaching and demand significant organisational transformation. Contractors must conduct thorough self-assessments of current security practices, implement necessary cybersecurity controls, develop comprehensive program documentation, and engage in readiness activities.
This requires substantial investment in both technical infrastructure and human capital, as organisations must build and maintain their security capabilities. The resource considerations extend beyond immediate compliance costs, and include ongoing maintenance, training, and continuous monitoring requirements.
Key Success Factors
Several critical factors will determine the success of CMMC implementation within organisations. Documentation emerges as a fundamental requirement, necessitating detailed security practice documentation, clear incident response procedures, and comprehensive audit trails. Continuous monitoring becomes increasingly important, requiring regular security assessments, ongoing vulnerability management, and performance tracking.
Strategic and Future Implications
The future implications of CMMC extend well beyond simple compliance requirements. The framework represents a fundamental transformation in the defence sector cybersecurity, creating a standardised approach to security practices across the supply chain. Early adopters who achieve higher levels of certification will gain strategic advantages in securing sensitive contracts, while demonstrating enhanced credibility with DoD partners. Most critically, CMMC strengthens the US’s ability to protect sensitive information against increasing threats, ultimately enhancing national security through improved supply chain resilience.
As noted by industry experts, failure to comply could result in exclusion from DoD contracts, posing significant risks to business operations and financial stability.
Conclusion: A Strategic Necessity for National Security
The success of this initiative will depend on careful coordination between government agencies, third-party assessors, and defence contractors. Through this collaborative effort, the DoD aims to create a more secure and resilient defence industrial base, better equipped to counter the evolving threat landscape of APTs. The implementation of CMMC therefore represents not only a regulatory requirement, but a strategic necessity for national security in the digital age.
References:
1. https://dodcio.defense.gov/Portals/0/Documents/CMMC/CMMC-FAQs.pdf
2. https://dodcio.defense.gov/cmmc/About/
3. https://dodcio.defense.gov/Portals/0/Images/CMMC/CMMC-Diagram.png
4. https://www.federalregister.gov/documents/2024/10/15/2024-22905/cybersecurity-maturity-model-certification-cmmc-program

