Striking a balance between offence and defence of cybersecurity: Purple Teaming
Striking a balance between offence and defence of cybersecurity: Purple Teaming
Security exercises, also known as security drills or simulations, are important for several reasons such as identifying vulnerabilities, testing of security incident response and meeting compliance requirements. These exercises are important tools for organisations to assess their security posture, improve incident response, raise awareness, and meet compliance requirements. In this article, we will be looking at a form of security testing that involves red, blue and purple teaming.
Understanding Red, Blue and Purple Teams
Red teaming and blue teaming are two types of security testing techniques that are commonly used by organisations to improve their security posture. The main difference between the two is the perspective they take when testing the organisation's security systems.
Red Team (Offence)
Red teaming involves simulating an attack against an organisation's security systems to identify vulnerabilities and weaknesses. The red team is typically made up of security professionals who are given the freedom to use any means necessary to breach the organisation's defences. The goal of red teaming is to identify areas where the organisation's security systems can be improved to better defend against real-world attacks.
Blue Team (Defence)
On the other hand, blue teaming involves defending against the simulated attacks launched by the red team. The blue team is typically made up of the organisation's security professionals who are responsible for protecting the organisation's assets. The goal of blue teaming is to identify gaps in the organisation's security defences and improve their ability to detect and respond to real-world attacks.
Purple Team (Combination)
Purple teaming is a collaborative approach that combines the benefits of both red and blue teaming to enhance an organisation's security posture. In purple teaming, the red team and blue team work together closely to identify vulnerabilities and improve security controls.
The red team simulates attacks and attempts to breach the organisation's security systems. The blue team then responds to the simulated attacks, identifies areas where their defences could be improved, and implements necessary changes. The red team provides feedback on the effectiveness of the blue team's response and the strength of the organisation's defences.
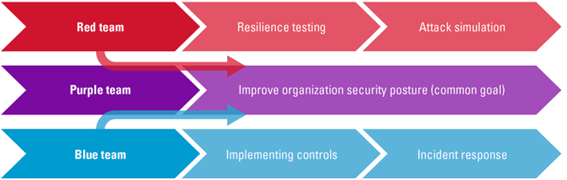
Figure 1: Difference between Red, Blue & Purple Team
Goal of Purple Teaming
The goal of purple teaming is to improve the overall security of the organisation by combining the offensive and defensive approaches of red and blue teaming. By working together, the red and blue teams can identify and address vulnerabilities more efficiently and effectively, reducing the risk of real-world attacks.
Purple teaming is particularly useful for organisations that have already established red and blue teaming programs and want to take their security testing to the next level. It can also be useful for organisations that are looking for a more collaborative approach to security testing that involves all stakeholders in the process.
Benefits of Combination of Red and Blue Teaming Exercise (Purple Teaming)
Red team and blue team exercises are security testing techniques that are commonly used by organisations to improve their security posture. In a red team exercise, a team of security professionals simulates an attack against an organisation to identify vulnerabilities in their security systems. In a blue team exercise, the organisation's security team defends against the simulated attack to identify areas where their security systems can be improved. The following are some ways in which red and blue team exercises can help an organisation:
Identify vulnerabilities: Red team exercises help organisations to identify weaknesses in their security systems that could be exploited by attackers. This information can be used to improve security controls and reduce the risk of a real-world attack.
Test response plans: Blue team exercises provide an opportunity to test the organisation's response plans and incident response procedures. This helps to identify gaps in the plans and improve the effectiveness of the response.
Increase awareness: Red and blue team exercises can increase awareness of security risks among employees and the management. This can help to create a culture of security within the organisation, and it also reduces the risk of security incidents that could be caused by human error.
Improve collaboration: Red and blue team exercises require collaboration between different teams within the organisation, such as the security team, IT team, and business units. This can help to improve communication and collaboration between these teams, which can be beneficial in responding to real-world security incidents.
Measure effectiveness: Red and blue team exercises provide a way to measure the effectiveness of security controls and procedures. This information can be used to make data-driven decisions about security investments and improvements.
Carrying out a successful Purple Teaming exercise
Below are the guidelines to conduct a purple teaming exercise.
1. Define objectives: Define the objectives of the purple team exercise that includes what the organisation wants to achieve, which systems or areas will be targeted, and what specific security controls will be tested.
2. Assemble the teams: Assemble the red and blue teams, including security professionals from within the organisation and external third-party security experts if necessary. Ensure that the teams have the appropriate skills and expertise to carry out their roles effectively.
3. Establish rules of engagement: Establish clear rules of engagement that define what the red team can and cannot do, as well as what the blue team can and cannot do in response to simulated attacks. This helps to ensure that the exercise is carried out safely and effectively.
4. Conducting the exercise: The red team simulates attacks against the organisation's security systems, while the blue team defends against the attacks and identifies areas where the organisation's defences can be improved. The teams work together closely, sharing information and collaborating on ways to improve the organisation's security posture.
5. Results analysis: Analyse the results of the purple team exercise, including the effectiveness of the organisation's security controls and the response of the blue team. Use this information to identify areas where the organisation's security posture can be improved.
6. Implementing improvements: Implement improvements to the organisation's security controls and procedures based on the results of the purple team exercise. This helps to reduce the risk of real-world attacks and improve the overall security posture of the organisation.
7. Continuous process: Conduct the purple team exercise on a regular basis (recommended annually) to ensure that the organisation's security posture continues to improve over time.
Summary
Purple Teaming does not focus exclusively on offence or defence, but it is a combination of both. They are designed to spot-check an organisation’s security posture to ensure that both the red and blue teams work together. It encourages both teams to share feedback and insights with one another. The key to success within an organisation with existing red and blue teams is to have constant communication among stakeholders and consistency in information sharing by adopting a purple teaming posture. To defend against evolving threats in cybersecurity, a comprehensive security measure needs to be in place, and this includes purple teaming, regular security audits and threat hunting.
BDO Cybersecurity Team has developed a track record over the years by providing cyber security services like incident response, network penetration testing, physical security, application security, and security research in various industries. Contact us to learn more on how to better manage and mitigate cybersecurity risks for a safer mind through our services.
Reference
https://www.bridewell.com/insights/blogs/detail/an-introduction-to-purple-teaming