In penetration testing, tools are important, but mindset is everything.
You can run a scanner and walk away with a PDF report. Or you can think like an attacker, ask the right questions, follow the wrong paths on purpose and uncover vulnerabilities no tool would ever detect.
This article is about cultivating that mindset, the adversarial lens. It’s about training your brain to spot weak trust assumptions, chain small bugs into real impact, and see applications the way attackers do.
What Makes a Hacker’s Mind Different?
The hacker’s brain doesn’t accept the front door. It looks for cracked windows, backdoors, or ways to climb in through the ventilation system.
This way of thinking is defined by:
-
Asking non-obvious questions
-
Looking past the “happy path”
-
Abusing logic and assumptions
-
Chaining edge cases into breakthroughs
Traits That Define the Adversarial Mindset
1. Narrative-Driven Exploitation
Good attackers build a storyline. Instead of randomly testing endpoints, they imagine how an attacker would approach a goal step-by-step.
Example Narrative:
“I’m a normal user. I need to get access to HR data. What can I touch? Can I modify any object? What roles have access? How can I escalate from here?”
This approach turns chaotic testing into targeted moves.
The flowchart below illustrates this exact thinking — chaining together predictable object IDs, data leaks, and SSRF abuse into a full privilege escalation path.

Figure 1: Flowchart of an example narrative to gain access to HR database.
2. Breaking Trust Boundaries
Hackers do not see systems as silos. They spot where trust crosses boundaries between frontend and backend and exploit it.
They ask:
-
Is the client trusted to sanitise input?
-
Is the API relying on hidden fields for authorisation?
-
Can a URL from the outside world touch internal systems?
Real-World Example: isAdmin in localStorage
A front-end sets isAdmin: false in localStorage. The backend trusts this flag and shows user-level data.
A real attacker changes the flag to true and the app leaks admin-only data.
Step 1: Original Client Request (as a low-privileged user)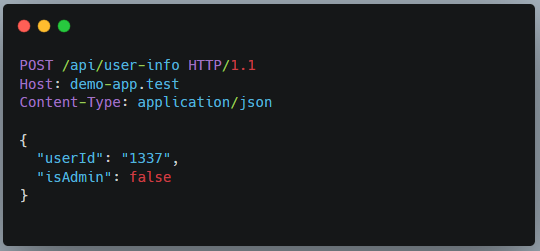
Step 2: Normal API Response (user-level access)
Step 3: Attacker Modifies Request Locally (Changes isAdmin to true)
Step 4: API Trusts the Value and Leaks Admin-Only Data
3. Attacking Assumptions, Not Just Code
Many developers build applications on implicit trust and hidden assumptions, such as:
-
“This parameter will never be modified.”
-
“Only the frontend can access this API.”
-
“This file is only used by admins.”
Hackers thrive by violating those assumptions in ways the developer did not anticipate.
Real-World Example: File Upload Bypass via MIME Type Mismatch
Let’s say a web application allows profile picture uploads but restricts file extensions to .jpg or .png. On the frontend, JavaScript performs file type checks. But the backend fails to validate the MIME type or sanitise the file content.
An attacker uploads a web shell like reverse.php.jpg , a PHP script disguised with a double extension. Since the backend stores the file in an executable directory (e.g., /uploads/), and Apache or Nginx interprets .php inside the name, the payload gets executed.
Step 1: Upload Payload with Double Extension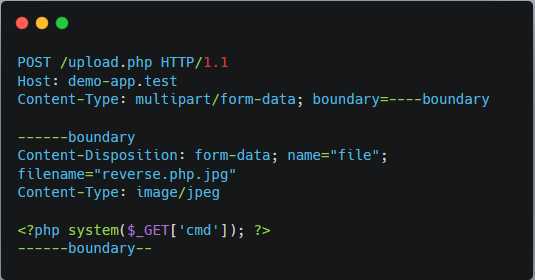
Step 2: Server Accepts the File
Step 3: Attacker Triggers Command Execution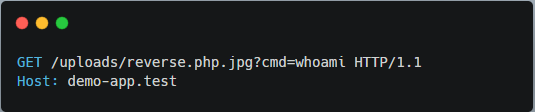
Step 4: Response from Backend
4. Weaponising “Non-Issues”
Many testers overlook minor flaws because they don’t trigger critical alerts. But attackers see these so-called “non-issues” as recon goldmines, subtle cracks they can wedge open into bigger compromises.
Common overlooked areas include:
-
Lack of rate-limiting on sensitive actions
-
Predictable URLs or file paths
-
Error messages that leak system behavior
Realistic Example: Email Enumeration via Password Reset
A login portal exposes different responses based on whether the email address exists. While this may seem harmless, it enables user enumeration, which can be weaponised during credential stuffing or phishing campaigns.
Step 1: Send Reset Request with Non-Existent Email
The HTTP Response: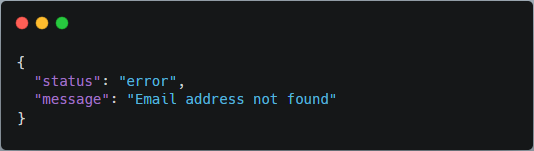
Step 2: Send Reset Request with Valid Email
The HTTP Response: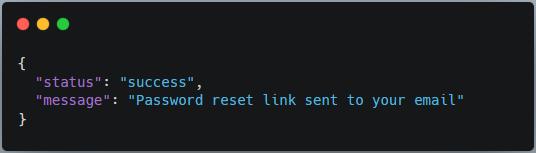
5. Chaining Micro Bugs into Full Compromise
Most automated scanners report issues in isolation, one bug at a time. But attackers think in chains. They combine small, “non-critical” findings into powerful multi-stage exploits that lead to full system compromise.
Realistic Attacker Storyline: From Enumeration to RCE
Let’s say you are testing a user account management portal. At first glance, nothing stands out: no RCE, no SQLi. But you piece together these:
Step 1: Email Enumeration
Response: "Password reset link sent"
Invalid email? "Email not found"
→ You now know which users exist.
Step 2: Rate Limit Bypass on Login
No delay or CAPTCHA after multiple failed attempts.
→ Allows brute-forcing with valid emails.
→ Login to a known account.
Step 3: IDOR in Profile Editing
→ You change another user’s profile by guessing their ID.
Step 4: Upload PHP Payload via File Upload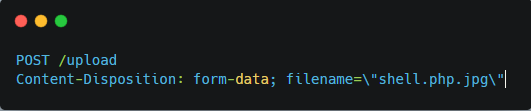
→ Backend stores it without validating extension/MIME properly
Step 5: Access File in Development Folder
→ Remote Code Execution (RCE) achieved.
Final Impact: Full Takeover
None of the above bugs alone is “critical.”
But when chained together:
-
Enumeration → Initial foothold
-
IDOR → Lateral access
-
Upload → Code execution
🧠 That is the adversarial mindset. Not “What’s the CVSS score?” but “How far can I go with what I have?”
Bonus Tactic: Lying to the Application
Here is one of my favorite mindset tricks: Lie to the app.
-
Spoof roles (e.g., change X-User-Role: user to admin)
-
Claim to be someone else (X-Forwarded-For, cookies, Referer header)
-
Say your file is safe when it’s not (Content-Type: image/jpeg for a PHP file)
Just like social engineers lie to humans, adversaries lie to applications.
Example: Bypassing IP Restrictions with X-Forwarded-For
Let’s say a web application restricts access to /admin based on IP — only accessible from 127.0.0.1.
Step 1: Normal User Request (Blocked)
The HTTP Response:
Step 2: Attacker Spoofs Internal IP
The HTTP Response:
Why this works:
Some applications naively use req.headers['x-forwarded-for'] or similar approaches to make trust decisions without validating the true source of the request (like req.socket.remoteAddress).
Mindset vs. Scanner Mentality
|
Scanner Mentality |
Adversarial Mindset |
|
Run tool. Wait for results. |
What happens if I bend the logic? |
|
No RCE found, nothing critical. |
Can I chain small flaws into something big? |
|
404 = dead end. |
Or maybe it’s just renamed or obfuscated? |
|
Only test authenticated role. |
What if I change tokens or spoof identities? |
Final Thoughts
Anyone can fire up Burp, Nmap or other scanning tools. But true pentesters, the ones who find the real issues, always ask deeper questions.
They do not settle for 200 OKs or CVE scans. They lie, probe, bend logic, and think from the perspective of someone who wants in, badly.
If you want to level up, focus less on tools, more on storylines. Ask questions that make devs uncomfortable. Do not scan, investigate.
“Every bug starts with a question the developer didn’t think you'd ask.”
References
-
OWASP Testing Guide v4 – Testing for Authorization Bypass: https://owasp.org/www-project-web-security-testing-guide/
-
PortSwigger Web Security Academy – Business Logic Vulnerabilities: https://portswigger.net/web-security/logic-flaws
-
HackTricks – Offensive Security Knowledge Base: https://book.hacktricks.xyz/
-
Google Project Zero Blog – Real-World Exploits and Research: https://googleprojectzero.blogspot.com/
-
PentesterLab – Attacker Thinking and Vulnerability Chains: https://pentesterlab.com/
-
The Hacker Mind Podcast – Inside the Attacker's Thought Process: https://thehackermind.com/
-
HTB & TryHackMe Platforms – Realistic labs to sharpen offensive mindset: https://tryhackme.com and https://www.hackthebox.com
-
Cybersecurity & Infrastructure Security Agency (CISA) – MITRE ATT&CK Framework: https://attack.mitre.org/
-
ChatGPT – AI-Powered Assistance for Red Teaming & Payload Simulation: https://chatgpt.com/

